
What Is Transaction Monitoring? Essential Insights for Security
At its heart, transaction monitoring is the process of keeping a close eye on customer transactions to spot anything that looks out of place. It’s like a digital neighborhood watch for your business, constantly scanning for patterns that might hint at illegal activities like money laundering, fraud, or even terrorist financing.
Unmasking Suspicious Activity with Transaction Monitoring

Imagine a security guard for your company’s finances. But instead of patrolling a physical building, this guard watches the constant flow of payments, deposits, and withdrawals. The main job? To flag any behavior that doesn't quite fit the customer's usual pattern.
This isn't just a "nice to have" feature; it's a critical part of staying on the right side of the law. Regulations like the Bank Secrecy Act (BSA) require financial institutions to have these systems in place. Without them, companies risk becoming unwilling accomplices in financial crime, facing massive fines and a damaged reputation. It's really the bedrock of any solid Anti-Money Laundering (AML) and Counter-Financing of Terrorism (CFT) strategy.
To make this a bit clearer, here’s a quick breakdown of what transaction monitoring is all about.
Transaction Monitoring At A Glance
| Component | Description |
|---|---|
| Who? | Financial institutions, crypto exchanges, and other regulated businesses. |
| What? | The ongoing review and analysis of customer transactions (deposits, withdrawals, transfers). |
| Why? | To detect and report suspicious activity, comply with AML/CFT regulations, and prevent financial crime. |
| How? | Using automated software that flags transactions based on predefined rules, risk profiles, and behavioral patterns. |
Essentially, it's a systematic way to separate the legitimate transactions from the potentially illegal ones.
How It Identifies Red Flags
So, what exactly is this digital guard looking for? It's all about spotting "red flags"—specific triggers programmed into the system that are often linked to financial crime. These can be surprisingly simple or incredibly complex, but they all represent a deviation from what’s considered normal.
Here are a few classic examples that would set off an alarm:
- Unusual Transaction Sizes: A customer who typically moves a few hundred dollars at a time suddenly wires $50,000.
- High Frequency of Transactions: An account that’s normally quiet suddenly lights up with dozens of small, back-to-back transactions.
- Geographic Risk: Money is moving to or from a country flagged as a high-risk jurisdiction for crime or terrorism.
- Structuring (or "Smurfing"): A series of deposits are made just under the $10,000 reporting threshold to try and fly under the radar.
The real magic of transaction monitoring is its ability to learn what "normal" looks like for each individual customer. Once that baseline is established, it becomes much easier to spot the outliers that need a human touch.
When a transaction triggers an alert, it doesn’t automatically mean a crime is happening. It's simply a signal for a compliance officer to step in, take a closer look, and figure out the story behind the numbers.
How The Transaction Monitoring Process Works
So, what does transaction monitoring actually look like in practice? To really get it, you need to peek under the hood. It’s less of a single action and more of a lifecycle—a sophisticated filtration system that sifts through every dollar your company handles. It starts with a sea of raw data and ends with a specific, actionable alert for your compliance team to dig into.
The whole thing kicks off with data collection. We're talking about gathering everything: every payment, deposit, transfer, and withdrawal. This information is pulled from multiple sources, creating a detailed picture that includes customer info, transaction amounts, locations, and timestamps.
With all that data in hand, the system moves into the automated analysis phase. This is where the magic happens. It isn't just a simple checklist; modern systems use a powerful one-two punch to sniff out potential trouble.
The Core Analytical Engine
The first layer of defense is a rules-based engine. Think of this as the bouncer at the door with a strict guest list. It's programmed with a clear set of instructions, and it flags any transaction that breaks a predefined rule. These rules aren't arbitrary—they're built on regulatory mandates and known patterns of criminal activity.
Here are a few classic rules that will almost always trigger an alert:
- Threshold Violations: Any transaction that sails past a certain dollar amount, like the $10,000 reporting threshold for currency transactions.
- Geographic Red Flags: Money zipping to or from countries known to be high-risk for money laundering or financing terrorism.
- Structuring (Smurfing): This is the classic "staying under the radar" tactic. The system spots a pattern of multiple smaller transactions designed to sneak just below reporting limits.
- Sanctions Screening: A mandatory check against global watchlists to make sure you're not doing business with sanctioned individuals, groups, or nations.
The second, smarter layer relies on behavioral analysis and anomaly detection. This is where the system gets personal. It builds a "normal" profile for each customer by learning their typical transaction sizes, frequency, and financial habits. When a customer suddenly does something out of character—even if it doesn’t break a specific rule—an alert gets triggered.
For instance, imagine a customer whose account activity consists of small, local debit card purchases. One day, they wire a large, unusual sum to an overseas account. That's a textbook anomaly. The system flags it not because a hard rule was broken, but because the behavior is completely out of the ordinary and therefore suspicious.
This simple infographic below captures this fundamental three-step flow, from raw data intake to the final alert.
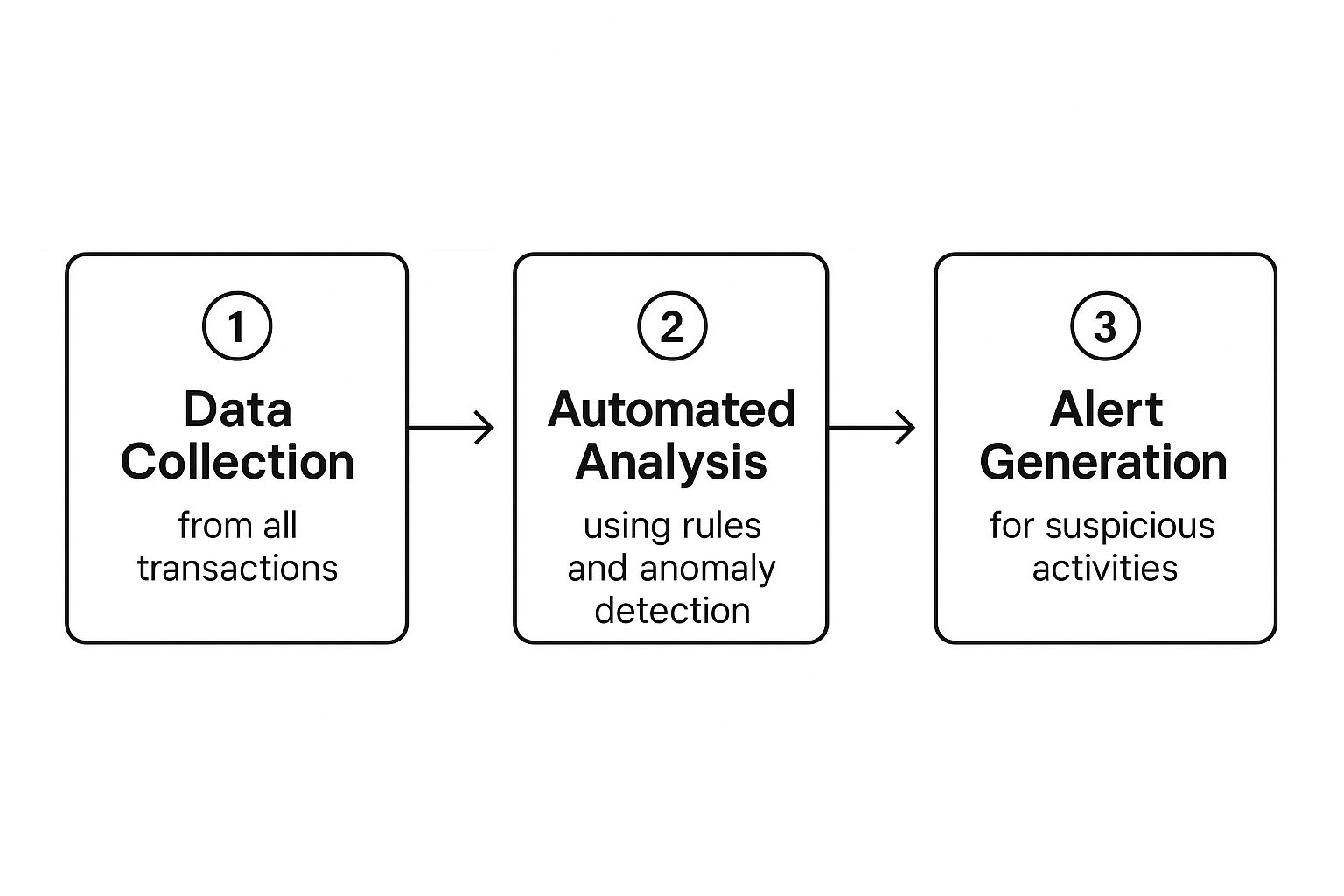
As you can see, the process is designed to turn a flood of financial data into focused, actionable intelligence. It helps your team zero in on the transactions that truly demand a closer look.
From Alert to Action
Once the system flags a transaction, the baton is passed from the machine to a human. A compliance analyst gets the alert and starts the real detective work. They’ll review the customer's entire history, the specifics of the transaction, and any other relevant context to figure out if it's a genuine risk or just a "false positive."
This investigation is a vital piece of the puzzle, ensuring that every financial record adds up correctly, a concept we explore in our guide on what payment reconciliation is.
If the analyst confirms that something fishy is going on, the final step is to file a Suspicious Activity Report (SAR). In the U.S., for example, this report goes to the Financial Crimes Enforcement Network (FinCEN).
A SAR is the official document that details the suspicious activity, and it becomes a crucial piece of intelligence for law enforcement agencies building cases against financial criminals. This closes the loop, turning a single digital flag into a real-world tool in the fight against crime.
Why Every Business Needs Transaction Monitoring

It’s one thing to know how transaction monitoring works, but it's another to truly grasp why it's become completely non-negotiable for modern businesses. Putting a solid monitoring system in place isn’t just a "nice-to-have" anymore. It's a fundamental part of staying in business, driven by two major forces: tough regulations and smart self-preservation.
You simply can’t afford to ignore this. Governments around the world have rolled out strict rules to fight financial crime, and the consequences for falling short are steep. Laws like the Bank Secrecy Act (BSA) in the U.S. require businesses to actively watch for and report any fishy financial activity. A failure here can lead to massive fines, business restrictions, and even criminal charges for executives.
Protecting Your Business From The Inside Out
Looking past the legal threats, good transaction monitoring is also your best defense against direct financial hits and damage to your reputation. Think of it as an insurance policy for your company's future health. Every fake chargeback you stop and every money laundering scheme you block is a direct win for your bottom line.
This kind of proactive defense is crucial for a few key reasons:
- Fraud Prevention: It stops financial losses dead in their tracks by catching and blocking fraudulent transactions before they can do real harm.
- Reputation Management: A single security breach or compliance slip-up can undo years of hard work building your brand. Strong monitoring proves to customers and partners that you’re a secure and trustworthy company.
- Operational Integrity: It keeps your payment systems clean, ensuring they're used for legitimate business. This protects your vital relationships with banks and payment processors.
Transaction monitoring shifts a business from a reactive stance—cleaning up messes after they happen—to a proactive one, where potential threats are neutralized before they can impact customers or the company's finances.
A Strategic Imperative In A Growing Market
The need for these systems isn't just talk; it's a rapidly growing global reality. Implementing strong transaction monitoring is especially critical in sectors like finance, where using analytics in the banking industry is essential for managing risk effectively.
The worldwide market for these solutions is exploding, which shows just how vital they've become. Valued at USD 11.8 billion, the market is expected to surge to USD 44.3 billion, growing at a compound annual rate of 14.2%. This growth is being driven by the boom in digital payments and the mounting pressure on businesses to meet AML and CTF regulations.
At the end of the day, transaction monitoring doesn’t work in a vacuum. It goes hand-in-hand with other compliance steps, like the initial identity verification process that is central to understanding https://blockbee.io/blog/post/what-is-kyc-in-crypto. By linking a verified identity to ongoing financial behavior, businesses build a complete, multi-layered defense against financial crime and secure their operations for the long haul.
The Shift From Manual Rules To Smart AI Monitoring
In the early days of transaction monitoring, the systems in place acted a lot like a nightclub bouncer with a very strict, very simple guest list. This traditional approach, known as rules-based monitoring, was built on a foundation of hard-coded, inflexible conditions.
A classic example? A rule might automatically flag every single transaction over $10,000, or perhaps any payment sent to a specific high-risk country. Simple, yes, but also incredibly noisy. The biggest problem with this method is the avalanche of false positives it creates. A legitimate business owner paying for new equipment and a money launderer would both trigger the exact same alert. This buries compliance teams in a mountain of notifications, forcing them to spend most of their day sifting through harmless activity instead of chasing down genuine threats.
The Rise Of Intelligent Monitoring
As financial criminals got smarter and their tactics more subtle, it became painfully obvious that a simple checklist wasn't going to cut it anymore. The industry needed a watchdog that could think, learn, and adapt on the fly. This need paved the way for integrating Artificial Intelligence (AI) and Machine Learning (ML) into transaction monitoring platforms.
Instead of just checking boxes, these modern systems learn what "normal" behavior looks like for every single customer. They build a dynamic, ever-evolving profile by analyzing thousands of data points, including:
- Typical transaction amounts and frequency
- The usual geographic locations for payments
- The time of day a customer is normally active
- The types of devices they use to make transactions
This intelligent profiling is a game-changer. It allows the system to spot subtle red flags that a rigid, rules-based engine would have completely missed.
For instance, a rules-based system would likely ignore five separate $1,500 transactions. An AI model, however, would immediately recognize this pattern as highly unusual for a customer who normally only spends $50 at a time. It would flag the activity as potential structuring, demanding a closer look.
How AI Delivers Pinpoint Accuracy
The real magic of AI is its ability to crunch massive datasets and uncover complex, hidden patterns in real-time. The growth of AI and data analytics has allowed transaction monitoring software to evolve beyond simple rule-following into creating predictive models that adapt to new threats. As data on the transaction monitoring software market shows, these technologies are crucial for improving both fraud detection and overall compliance efficiency.
This shift couldn't come at a better time. With digital payments exploding worldwide, new vulnerabilities are constantly emerging, and the job of monitoring it all is getting more complex by the day.
Rules-Based vs AI-Powered Monitoring
To really understand the difference, it helps to see the two approaches side-by-side. The old way was about setting static traps, while the new way is about having an intelligent hunter that learns the terrain.
| Feature | Rules-Based Systems | AI-Powered Systems |
|---|---|---|
| Logic | Static, predefined rules (e.g., "flag all transactions > $10,000"). | Dynamic, adaptive learning based on behavioral baselines. |
| Detection | Catches known, obvious patterns of illicit activity. | Identifies subtle, unknown, and emerging threat patterns. |
| False Positives | Very high, leading to significant wasted effort. | Significantly lower, allowing teams to focus on real risk. |
| Adaptability | Slow. Rules must be manually updated by analysts. | Fast. Models learn and adapt automatically from new data. |
| Context | Lacks context. A transaction is either "good" or "bad." | Understands context by analyzing a customer's entire history. |
Ultimately, AI-powered systems don't just find more bad guys; they also clear the innocent faster.
By understanding context and constantly learning, AI-driven monitoring slashes the number of false positives. This frees up your compliance experts to focus their valuable time and energy on the highest-risk cases, making the entire operation more effective at stopping financial crime where it starts.
Tackling the Toughest Challenges in Transaction Monitoring

Putting an effective transaction monitoring system in place is anything but a "set it and forget it" project. Even the most sophisticated platforms run into serious operational hurdles that can bury compliance teams and leave a business wide open to risk. These aren't just occasional hiccups; they're the daily reality of fighting financial crime.
One of the biggest issues is simply the mind-boggling volume and speed of transactions. The explosion of digital banking, e-commerce, and crypto has unleashed a tidal wave of data that older systems just can't keep up with. Think about it: the U.S. transaction monitoring market is on track to hit nearly $20 billion, fueled by a 16.6% CAGR from this digital boom. This incredible scale makes it far too easy for clever criminal activity to get lost in the noise.
Navigating False Positives and Evolving Threats
Another persistent headache is the flood of false positives. These are perfectly legitimate transactions that get flagged as suspicious, and they can completely swamp a compliance team. When your analysts are spending all day chasing ghosts, their focus gets pulled away from genuine threats. It's not just inefficient—it’s dangerous.
At the same time, the bad actors are always one step ahead. Financial criminals are constantly inventing new ways to sidestep detection systems. This creates a relentless cat-and-mouse game where your monitoring rules have to adapt constantly. A static, rules-based system just won’t cut it anymore.
The core challenge isn't just finding a needle in a haystack. It's realizing the needles are constantly changing shape and the haystack is growing bigger every second.
The Complexity of Integration and Data Privacy
Finally, getting all the technology to talk to each other is a huge operational lift. Effective monitoring relies on pulling together data from all over the business, which makes strong systems integration absolutely essential. A fragmented tech setup creates data silos, preventing you from getting a full picture of customer activity and leaving dangerous blind spots.
On top of all that, you have to navigate a minefield of data privacy regulations like GDPR. The goal is to gather enough data to spot illicit activity without crossing legal lines or breaking customer trust. It’s a delicate balancing act that demands a smart, well-designed system. You can dive deeper into these complexities in our detailed guide on anti-money laundering transaction monitoring.
Common Questions About Transaction Monitoring
As you start to wrap your head around transaction monitoring, a few questions almost always pop up. Let's tackle them head-on, as the answers really help clarify how this all works in the real world.
Is Transaction Monitoring The Same As Fraud Detection?
That's a great question, and while they're definitely related, they are not the same thing.
Think of it this way: fraud detection is like having a security guard focused specifically on stopping shoplifters. Their job is to prevent direct theft that hurts the store and its customers, like credit card fraud or someone hacking into an account.
Transaction monitoring is more like the entire security system for the whole building. It includes that guard (fraud detection), but it's also watching for bigger, more complex threats, especially Anti-Money Laundering (AML) compliance. Its job is to spot any kind of illegal financial activity, not just the obvious theft.
How Does This Work For Cryptocurrencies?
Monitoring crypto transactions is a whole different ball game. The pseudo-anonymous nature of wallets and the sheer speed of global blockchain transfers make tracking funds much trickier than following a paper trail in traditional banking.
Your standard monitoring tools just can't keep up. You need specialized software that can dig into public blockchain data, connect the dots between anonymous addresses and known illicit actors, and flag sneaky patterns like "chain hopping" through mixing services. For any business in the crypto space, these tools aren't just a nice-to-have; they're essential for staying compliant.
Do Small Businesses Really Need Transaction Monitoring?
Without a doubt. In fact, criminals often go after smaller businesses precisely because they assume their defenses are weaker. A single money laundering incident or a major fraudulent transaction can be a knockout blow for a small company.
The hard truth is that regulators don't give small businesses a pass. If you handle payments, you're expected to have AML and fraud prevention measures in place. Pretending you don't need it is a massive financial and legal gamble.
The good news is that you don't need a huge compliance department anymore. Modern transaction monitoring platforms are built to scale, offering powerful, affordable protection that fits the budget of a small business. It’s a straightforward way to protect your operations and show customers you can be trusted.
Ready to secure your crypto payments with a seamless, non-custodial solution? BlockBee provides robust tools for businesses of all sizes. Learn more about our crypto payment gateway and start accepting cryptocurrency with confidence.
