
Anti Money Laundering Transaction Monitoring: Essential Guide
At its core, anti money laundering (AML) transaction monitoring is how financial institutions keep a constant watch on customer transactions to spot patterns that might signal financial crime. Think of it as a digital detective, tirelessly sifting through millions of daily financial activities to find any suspicious behavior that needs a closer look.
What Is AML Transaction Monitoring Really?

Picture a security guard trying to watch over a massive, bustling city. It’s physically impossible for one person to track every single movement. But what if that guard had a city-wide network of smart cameras, automatically alerting them to anything unusual—a car speeding down a one-way street the wrong way or someone tampering with a lock? That’s exactly what AML transaction monitoring does for the financial system.
It’s not about some poor soul manually checking every single wire transfer or deposit. Instead, it’s a systematic, tech-driven process that serves as a financial institution's first line of defense against dirty money. This system is always running, scanning for transactions that don't fit a customer's usual behavior or that match known patterns of criminal activity.
The Core Purpose And Function
The main goal here is simple: detect and report suspicious activities that could be tied to money laundering, terrorist financing, or other financial crimes. Without this, criminal groups could effortlessly funnel illegal profits through legitimate banks, making their money appear clean.
And the scale of the problem is staggering. The United States alone is estimated to process a mind-boggling $300 billion in laundered funds every year, which has led regulators to get much tougher. You can dig into these global financial crime statistics to really grasp the scope of the issue.
This is why ongoing analysis is so crucial. It ensures that institutions are meeting their legal and moral duties to prevent their services from being used for crime.
To give you a better idea of what these systems actually do, let's break down their essential tasks.
Core Functions of AML Transaction Monitoring
This table breaks down the essential functions of an AML transaction monitoring program, giving you a quick overview of its key responsibilities.
| Function | Description |
|---|---|
| Pattern Recognition | Identifies sequences of transactions that are red flags. A classic example is "structuring," where multiple small deposits are made to avoid triggering reporting thresholds. |
| Anomaly Detection | Flags behavior that just doesn't add up with a customer's known profile. Think of a sudden, large international transfer from an account that's been dormant for years. |
| Risk Assessment | Prioritizes alerts by scoring them based on the customer's risk level, the type of transaction, and the geographic locations involved. |
Ultimately, these functions work together to ensure that compliance teams aren't chasing shadows.
At its heart, transaction monitoring is about separating the signal from the noise. It distinguishes the handful of potentially illicit transactions from the millions of legitimate ones that occur every day, protecting both the institution and the integrity of the broader financial ecosystem.
By automating this first layer of review, compliance teams can pour their energy and expertise into investigating the activities that pose a real threat. This proactive stance is the backbone of any strong AML program and a non-negotiable requirement from regulators around the world.
How a Transaction Monitoring System Works

To really get a handle on anti money laundering transaction monitoring, picture it as a high-tech filter. It’s a process designed to let millions of legitimate transactions flow through seamlessly while catching the few that are genuinely risky.
It all starts with data—and lots of it. A monitoring system first needs to pull in a huge amount of information from all over the place. We’re talking customer profiles, account histories, and payment details from both your own internal records and external sources.
Before any analysis can happen, this raw data needs to be cleaned up. The system standardizes everything so dates, currencies, and names are all in a consistent format. This step is absolutely critical; bad data leads to missed red flags or, just as bad, a mountain of false alarms for your team to dig through.
Data Analysis and Rule Application
With clean, organized data, the real work begins. The system runs every single transaction through a gauntlet of pre-set rules and sophisticated models. Think of these rules as tripwires, carefully placed to catch specific, known patterns of criminal behavior.
Some rules are straightforward. For instance, a simple rule might flag any cash deposit over $10,000, a threshold that automatically requires a Currency Transaction Report (CTR) in the United States.
Others are more nuanced. A complex rule could be designed to spot a series of smaller transactions that, when added up, cleverly duck just under that $10,000 limit—a classic red flag for structuring. This all happens continuously, often in real-time, catching suspicious activity the moment it occurs.
From Triggered Rule to Generated Alert
When a transaction breaks one of these rules, the system doesn't just block it. Instead, it generates an alert. This is essentially a digital tap on the shoulder for the compliance team, signaling that something needs a closer look from a human.
Each alert packages up all the necessary information for an initial review:
- Customer Information: Who is involved?
- Transaction Details: What was the amount, date, and method?
- The Triggering Rule: Why was this specific activity flagged?
- Historical Context: How does this compare to the customer’s usual behavior?
It's important to remember that an alert is not an accusation. It's a prompt. It’s the system telling a trained analyst, "Hey, this looks a bit odd—can you use your expertise to figure out if it's a real problem?"
This smart approach helps analysts zero in on the activities that pose the greatest risk, rather than getting lost in the noise.
The Analyst Investigation Workflow
Once an alert is created, it lands in a queue for a compliance analyst. This is where human intuition and investigative skills take over. The analyst’s job is to dig into the context and decide if the flagged activity is truly suspicious.
Let's walk through a classic example: structuring.
- The Alert: The system flags an account that just received five separate cash deposits of $9,500 on five consecutive days, each at a different bank branch. This pattern trips a rule designed to catch people trying to stay under the $10,000 reporting radar.
- The Investigation: The analyst pulls up the customer’s file. They run a small business that usually sees small, infrequent payments. This sudden rush of large, structured cash deposits is a major departure from their normal activity.
- The Decision: After reviewing the evidence, the analyst can't find a legitimate business reason for this bizarre pattern. They conclude the activity is suspicious and move to file a Suspicious Activity Report (SAR) with the proper authorities, like the Financial Crimes Enforcement Network (FinCEN) in the U.S.
This loop—from automated detection to human verification—is the heart of effective anti money laundering transaction monitoring. It blends the raw power of technology to sift through data with the irreplaceable critical thinking of a skilled professional. This process has also become vital for businesses in the digital asset space. You can learn more by checking out our guide on how to add crypto payments to your website.
The Shift From Static Rules To Smart AI
For years, AML transaction monitoring was a bit like a nightclub bouncer with a very strict, unchanging guest list. The system ran on simple "if-then" logic. If a transaction went over a certain amount, it got flagged. If a customer made too many deposits in a week, an alert was triggered. This was the era of static, rule-based monitoring.
These rigid rules were a necessary first step, but they came with a huge flaw: they were loud and often wrong. Because they couldn't understand context or nuance, they generated a massive volume of "false positives"—alerts on perfectly legitimate activity. This buried compliance teams in unproductive work, forcing them to spend countless hours clearing innocent alerts instead of investigating real threats.
This created a dangerous paradox. While analysts were swamped with noise, sophisticated criminals learned how to fly under the radar. They designed laundering schemes that were just too complex for simple, static rules to catch, effectively exploiting the system's blind spots.
The Limits Of Traditional Rules
The biggest problem with a purely rule-based approach is that it can't adapt. Criminals are constantly changing their methods, but static rules, by definition, don't. A rule written last year might be completely useless against a new money laundering technique emerging today.
This rigidity leads to several major weaknesses:
- High False Positive Rates: It's not uncommon for analysts to spend up to 95% of their time investigating alerts that turn out to be harmless. That's a massive drain on resources.
- Inability to Detect New Threats: Static rules can only find what they are specifically programmed to look for, leaving institutions vulnerable to new and complex laundering schemes.
- Operational Inefficiency: The sheer volume of alerts means you need bigger compliance teams, driving up operational costs without necessarily making you any better at catching criminals.
This is where the move to artificial intelligence and machine learning completely changes the game.
AI And Machine Learning: The New Standard
Modern AML transaction monitoring has moved way beyond simple tripwires. It now uses smart AI and machine learning models that act less like a bouncer with a list and more like an experienced detective who develops a feel for the crowd.
Instead of just following rigid commands, these systems learn from historical data. They analyze billions of transactions to understand what "normal" behavior actually looks like for each individual customer. This shift is where tools like predictive analytics in banking are making a real impact, helping to spot complex patterns of illicit activity that were previously invisible.
AI doesn't just check if a transaction breaks a rule; it asks if the transaction makes sense. It analyzes the who, what, when, where, and why behind the activity, looking for subtle deviations that a static rule would completely miss.
This contextual understanding is a monumental leap forward. A recent report highlighted that financial institutions are adopting machine learning to boost their detection accuracy, reducing false positives by as much as 40%. This means analysts can finally stop chasing ghosts and focus their expertise on the highest-risk cases.
The infographic below shows some of the top laundering methods that both old and new systems are designed to detect.
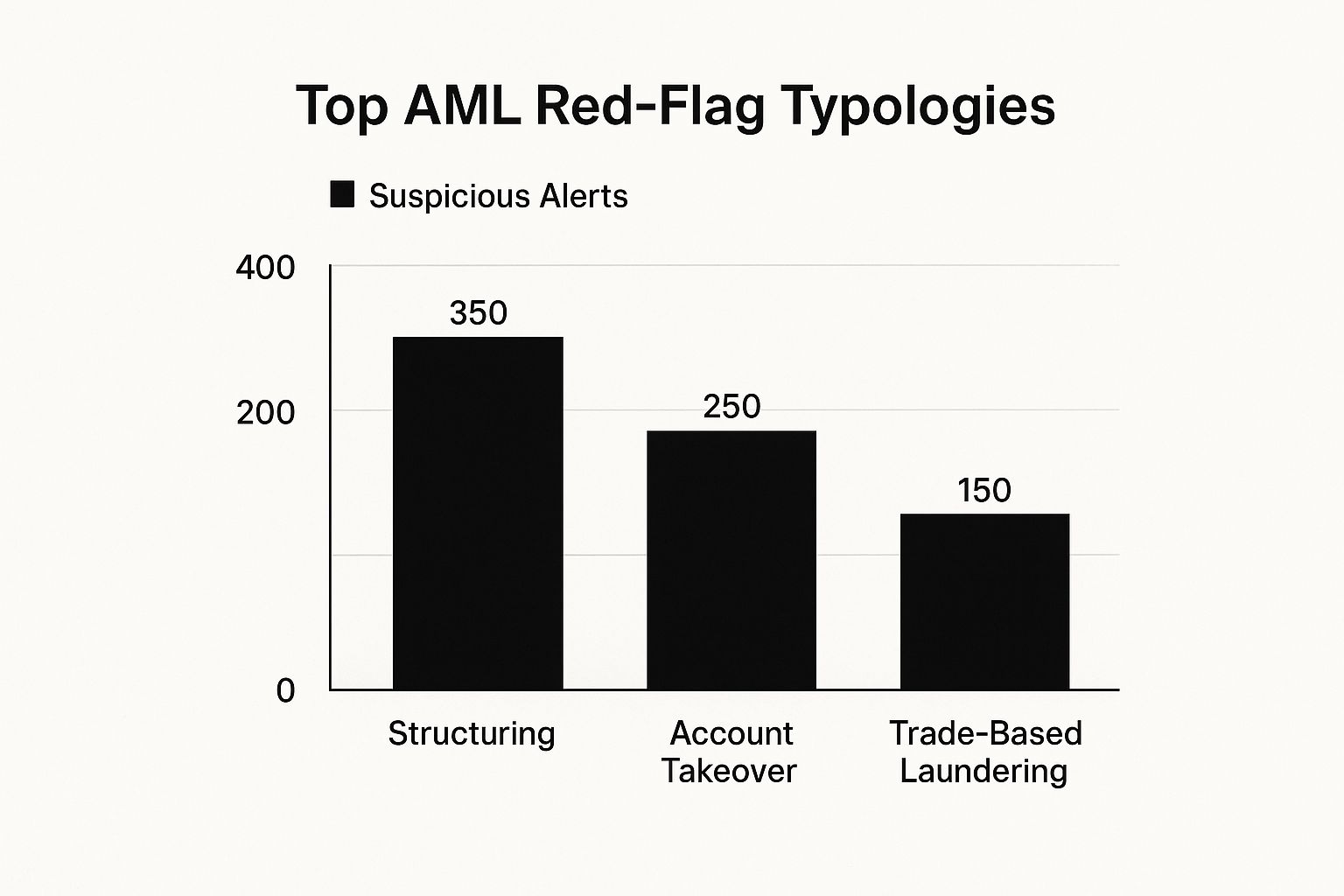
The chart clearly shows how varied these threats can be, which really underscores the need for a dynamic system that can identify all sorts of criminal behaviors.
To see the difference clearly, let's break down how these two approaches stack up side-by-side.
Comparing Rule-Based vs AI-Powered Monitoring
This table offers a side-by-side look at the key differences between traditional and modern AML monitoring systems, highlighting advances in efficiency and effectiveness.
| Feature | Traditional Rule-Based Systems | Modern AI-Powered Systems |
|---|---|---|
| Detection Method | Relies on pre-defined "if-then" rules and fixed thresholds. | Uses machine learning to analyze behavior and identify anomalies. |
| Adaptability | Static. Rules must be manually updated to address new threats. | Dynamic. Models learn and adapt to new criminal typologies over time. |
| False Positives | Generates a very high volume, often over 90%. | Significantly reduces false positives, often by 40% or more. |
| Contextual Analysis | Lacks context. A $10,000 transaction is just a number. | Provides deep context. Knows if that $10,000 is normal for that specific customer. |
| Efficiency | Labor-intensive, requiring large teams to review endless alerts. | Frees up analysts to focus on high-priority, complex investigations. |
| Threat Coverage | Limited to known and pre-programmed money laundering patterns. | Can uncover novel, complex, and previously unknown laundering schemes. |
Ultimately, while rule-based systems laid the foundation, AI-powered monitoring is what allows institutions to move from a reactive, checklist-based approach to a proactive, intelligence-driven one.
Building Your Modern AML Monitoring Program

Putting together a modern anti money laundering transaction monitoring program is a lot like building a high-tech security system for a skyscraper. You can't just put one camera on the front door and call it a day. You need a complete, integrated network of components working in concert to cover every angle.
A truly effective program rests on several key pillars. If you neglect even one, you're leaving a weak spot that criminals will happily exploit—and that regulators are sure to find. Think of this as the architectural blueprint for a strong, compliant, and defensible monitoring framework.
The Foundation: Data Integration
In the world of AML monitoring, everything begins and ends with data. Before you can spot a single red flag, you have to collect complete and accurate information from all corners of your business. This is the bedrock of your entire program.
Effective data integration is about pulling information from different systems into one unified view. We're not just talking about transaction records. This includes:
- Customer Profiles: Everything you gather during onboarding and your Know Your Customer (KYC) checks.
- Transaction Histories: A full log of all payments, transfers, and other account activities.
- External Data: Information from third-party watchlists, sanctions lists, and adverse media reports.
If your data isn't clean and centralized, even the most sophisticated AI models will stumble. A solid AML program also depends on ironclad data security. To learn more, it's worth exploring key strategies for data security compliance to ensure this sensitive information stays protected.
Intelligent Customer Segmentation
Let's be realistic: not all customers pose the same risk. Treating a local coffee shop owner with the same scrutiny as a high-net-worth individual with complex international dealings is both inefficient and ineffective. This is where intelligent customer segmentation makes all the difference.
By grouping customers into risk-based categories, you can apply the right level of monitoring. For example, a low-risk domestic customer might be monitored with a standard set of rules. On the other hand, a high-risk Politically Exposed Person (PEP) would trigger more intense, ongoing analysis. This risk-based approach lets you focus your resources where they matter most.
Customer segmentation transforms your AML program from a one-size-fits-all net into a set of precision tools. It enables you to apply the right level of monitoring to the right customer, drastically improving efficiency and detection accuracy.
This segmentation can't be a "set it and forget it" process. A customer's risk profile can change, and your system needs to be smart enough to adapt when new information comes to light or their transaction patterns shift.
A Flexible and Tunable Rules Engine
While AI gets a lot of the spotlight, a powerful rules engine is still an essential part of the toolkit. This is where you define the specific red flags you're looking for, like transactions that breach certain thresholds or involve high-risk countries.
A modern rules engine has to be incredibly flexible and easy to adjust. Compliance teams need to be able to create, test, and tweak rules on the fly, without getting stuck in a long IT queue. This agility is vital for responding to new regulatory guidance or emerging criminal tactics. The ability to fine-tune rules is also your best weapon against the constant headache of false positives, making sure your analysts' time is spent on real threats.
This flexibility is particularly critical for businesses adopting newer payment technologies. It’s a good idea to understand the basics of how to accept crypto payments for your business as this space continues to grow.
Streamlined Case Management Workflow
So, your system flags an alert. What now? A streamlined case management workflow is the operational heart of your AML program. It gives your investigators the tools they need to efficiently manage, research, and resolve alerts.
A top-notch case management system should provide:
- A Centralized Dashboard: A clear, prioritized view of all open alerts for analysts.
- Integrated Data Access: All relevant customer and transaction info right at the investigator's fingertips.
- Collaborative Tools: A way for team members to share notes and escalate tricky cases.
- A Clear Audit Trail: A documented record of every step taken during an investigation for regulatory review.
This ensures every alert is handled consistently and thoroughly, creating a defensible record of your compliance efforts and helping your team make faster, better-informed decisions.
Navigating Common AML Monitoring Challenges
Getting a solid anti money laundering transaction monitoring program up and running is a huge win, but that’s really just the starting line. Even the sharpest systems hit snags that can weaken defenses and bleed resources.
The key is to see these challenges coming. In the trenches, compliance teams are constantly wrestling with three big ones: messy data, a never-ending flood of false positive alerts, and the relentless pressure to keep up with sophisticated criminal schemes.
If you ignore any one of these, you're creating serious blind spots. Let's dig into what these roadblocks look like in the real world and how to get around them.
Tackling Poor Data Quality
Think of your transaction monitoring system as a high-performance engine. It needs clean fuel to run properly. If you're pumping in messy, incomplete, or jumbled data, you can’t expect it to perform. You'll miss real threats and chase down bogus alerts.
Bad data is one of the most persistent—and damaging—headaches in AML. It can pop up from anywhere: simple typos during manual entry, glitches during a system migration, or different teams using different formatting.
The best defense is a strong data governance framework. This isn't just about rules; it's about assigning clear ownership and setting quality standards right at the source. Putting automated data validation checks in place before information ever hits your monitoring system is a game-changer. It lets you catch and fix errors on the front end, making sure your entire analytics process is built on a solid, reliable foundation.
Taming The Flood Of False Positives
Ask any compliance analyst what their biggest frustration is, and they'll likely say "false positives." It's the sheer volume of alerts triggered by perfectly legitimate transactions that grinds teams down, drains their time, and balloons operational costs.
When investigators spend most of their day sifting through harmless noise, they have less mental energy for the truly suspicious stuff. This isn't just inefficient; it burns people out and dramatically increases the risk that a genuine threat gets lost in the shuffle.
A high false positive rate isn't just an inefficiency—it's a critical vulnerability. It creates a "boy who cried wolf" scenario where analysts become desensitized to alerts, potentially missing the one that truly matters.
To cut through the noise, you need to get smarter with your system's tuning and segment your customers more granularly. Don't just set your rules and forget them. Constantly review how they’re performing. For instance, if a certain rule keeps flagging normal activity for a specific group of customers, it’s time to tweak its thresholds. This kind of iterative refinement helps your system learn from its own history and become much more precise over time.
Staying Ahead Of Evolving Criminal Tactics
Criminals are creative—they don't use the same playbook forever. They're constantly finding new ways to wash money and poke holes in the financial system. If your monitoring program isn't evolving right alongside them, it’ll be obsolete before you know it.
This is a constant cat-and-mouse game, and the scale is staggering. Even with all our technology, law enforcement manages to seize less than 1% of illicit funds, which was estimated to be a whopping $3.1 trillion in 2023. You can get a better sense of where things are heading by exploring the future of financial crime compliance.
Keeping pace requires a proactive, vigilant culture, not just better software.
- Share Threat Intelligence: Get involved in industry forums and information-sharing networks. Knowing the latest money laundering typologies is half the battle.
- Pressure-Test Your Models: Don't wait for a real event to find a weakness. Regularly test your models and rules against known and emerging criminal schemes to see where your coverage might be thin.
- Bring in AI and Machine Learning: Modern AI-powered systems can spot complex and unusual patterns that your static, rule-based systems would completely miss. They adapt as criminal behavior changes.
By tackling these challenges with a mix of solid governance, smart technology, and a forward-thinking mindset, you can build an anti money laundering transaction monitoring program that’s not just effective today, but resilient enough for whatever comes next.
AML Transaction Monitoring FAQ
Diving into the world of anti-money laundering transaction monitoring can feel like learning a new language. Let's clear up some of the most common questions people have, breaking down the key concepts into simple, practical answers.
What Is The Difference Between Monitoring and Screening?
It's easy to get these two mixed up, but they play very different roles in your compliance strategy. The best way to think about it is that screening is like a bouncer at a club, while monitoring is the security camera system inside.
- Transaction Screening: This is the bouncer. It happens in real-time, before a transaction goes through. It checks the names and details of the people involved against official sanctions lists and watchlists. If there's a match, the transaction is blocked right there at the door.
- Transaction Monitoring: This is the camera system. It kicks in after transactions are complete, looking at a customer's behavior over time. It's designed to spot patterns that might look innocent on their own but become suspicious when viewed together, like a customer suddenly sending large sums of money to a high-risk country.
Screening is about stopping known criminals from getting in. Monitoring is about catching suspicious activity from anyone, even if they initially looked clean.
Screening asks, "Who is this person in this one transaction?" Monitoring asks, "What has this person been doing over time?"
How Often Should AML Rules Be Updated?
There isn't a single "right" answer here, but the worst thing you can do is "set it and forget it." Criminals are constantly changing their tactics, and regulators are always updating their expectations. Your AML rules need to keep pace.
As a rule of thumb, a full-blown, formal review of your entire rule set should happen at least once a year. But the real work is continuous. You should be ready to adjust your rules whenever:
- Regulators or industry groups flag a new money laundering scheme.
- Your company launches a new service or expands to a new country.
- You notice a specific rule is flagging way too many harmless transactions (creating a mountain of false positives).
Treating your rule set as a living document is the only way to stay ahead of the curve and maintain an effective anti-money laundering transaction monitoring program.
What Are The First Steps For A Small Business?
If you're running a small business, the idea of building an AML program from scratch can be intimidating. The secret is to start smart and build from a solid, risk-based foundation.
- Start with a Risk Assessment: Before you do anything else, you have to understand your specific weak spots. Are you serving customers in high-risk regions? Does your business model attract anonymous transactions? An honest assessment will tell you where to focus your efforts.
- Write Down Your Policies: Create a clear, simple document that outlines your AML procedures. Define what a "suspicious transaction" looks like for your specific business and what your team should do when they spot one.
- Pick the Right Tools: You probably don't need a massive, enterprise-grade system on day one. Look for a solution that fits your current size and risk level but has the ability to grow with your business.
Even for small businesses, getting a handle on how money moves is essential, particularly with digital currencies. Understanding the basics, such as what is a Bitcoin address, is a great starting point for managing crypto-related risks.
Ready to secure your crypto transactions with a reliable, non-custodial solution? BlockBee provides a powerful payment gateway with robust features, easy integration, and low fees, allowing you to accept over 70 cryptocurrencies effortlessly. https://blockbee.io
