
What is payment tokenization? How it protects your data
At its core, payment tokenization is a security method that swaps out sensitive data—like your 16-digit credit card number—with a unique, non-sensitive stand-in called a token. This token acts as a substitute, allowing payments to be processed without ever exposing the actual account details. Think of it as a digital shield.
How Tokenization Makes Digital Payments Safer
The best way to understand tokenization is with an analogy. Imagine you're at a casino. Instead of carrying a wad of cash from table to table, you exchange it for chips. Those chips have value inside the casino, but if someone steals them, they're just useless pieces of plastic on the outside.
Payment tokenization works the exact same way. It takes your valuable credit card number and swaps it for a randomly generated "chip"—the token.
This token is a string of characters that has no mathematical relationship to your original card number. So, if a hacker manages to steal it during a data breach, it's completely worthless to them. They can't reverse-engineer it to figure out your actual card details. This powerful security layer is what protects your data during online checkouts, in-app purchases, and with mobile wallets like Apple Pay and Google Pay.
What this means for businesses is huge. They can still offer convenient features like saved cards for one-click checkouts, but without the massive risk of storing sensitive cardholder information on their own servers. This separation of data is key to building customer trust and simplifying security compliance.
Tokenization works by removing the actual Primary Account Number (PAN) from the transaction flow entirely. This simple act devalues the data for potential thieves, making it a foundational element of any modern payment security plan.
Getting this to work requires a few different players to coordinate perfectly behind the scenes. A good payment platform definition will always include these kinds of integrated security measures, which depend on a clear division of responsibility.
Key Players in the Payment Tokenization Process
Here’s a breakdown of who does what in a typical tokenized transaction, showing how each entity plays a specific role in keeping payment data safe.
| Entity | Role in Tokenization | Primary Responsibility |
|---|---|---|
| Merchant | Initiates the tokenization request | Captures customer payment information securely and requests a token instead of storing the card number. |
| Payment Gateway | Securely transmits data | Transmits the card details to the tokenization provider and returns the generated token to the merchant. |
| Token Vault | Stores sensitive data | A highly secure, centralized server that stores the original card number and maps it to its corresponding token. |
| Card Network | Issues and manages tokens | (e.g., Visa, Mastercard) Often provides the tokenization service, ensuring tokens meet security standards. |
As you can see, it's a collaborative effort. The merchant never has to handle the raw card number directly, and the sensitive data is locked away in a secure vault, managed by entities with the highest levels of security.
How the Tokenization Process Works Step-by-Step
It's one thing to talk about tokenization as an idea, but seeing how it works in real-time really clears things up. From the moment you type in your card number to the final "approved" message, a lightning-fast, highly secure chain of events happens in the background. This whole dance is designed to make sure a merchant never has to touch—or store—your actual card details, which takes the risk of theft right off the table.
So, let's break down exactly what happens during a typical tokenized transaction. It all happens in a few seconds, but a lot is going on.
This visual gives you a quick snapshot of the core idea: your sensitive card data gets swapped for a secure token, and that token is what the merchant uses to handle the payment.
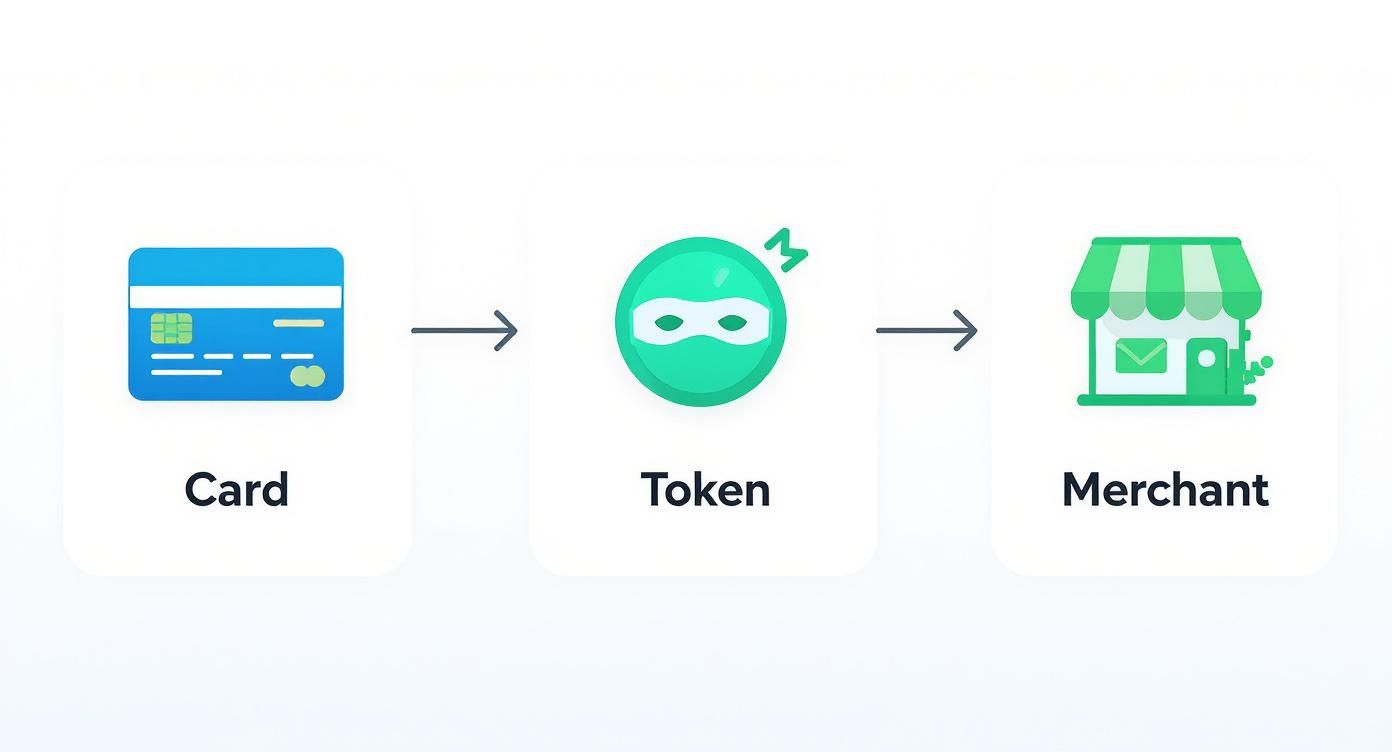
As you can see, the original card number is kept safely locked away, far from the merchant's system.
The Four Core Stages of Tokenization
Even though it feels instant, the process has four distinct stages. Each step involves a different player—from your web browser to the payment gateway to a secure "token vault"—all talking to each other seamlessly.
1. Data Capture: It all starts when a customer enters their credit card info on a checkout page or at a point-of-sale terminal. That sensitive data is immediately encrypted before it goes anywhere.
2. Token Request: The merchant’s system doesn't hold onto that data. Instead, its payment gateway zips the encrypted card info over to a specialized, ultra-secure token vault. The merchant is basically asking the vault, "Can you create a secure placeholder for this?" To get a better feel for how systems communicate like this, check out our guide on payment gateway API integration.
3. Token Generation and Storage: Inside its secure environment, the token vault decrypts the information and safely stores the real card number, known as the Primary Account Number (PAN). It then generates a brand-new, unique token that has no mathematical link to the original number. This new token is what gets sent back to the merchant.
4. Transaction Processing: Now the merchant has the token, not the PAN. For this transaction and any future ones (like subscriptions), the merchant just sends the token to their payment processor. The processor uses it as a key to look up the actual card details from the vault and run the charge with card networks like Visa or Mastercard.
This flow keeps the customer's actual card number locked down in the vault, while the token does all the traveling through systems that might be less secure.
The big idea here is that by swapping sensitive data for a token, you remove that data from the merchant's environment entirely. This single move is the key to simplifying PCI DSS compliance and dramatically reducing the damage a data breach could cause.
The explosive growth of this technology speaks for itself. The global tokenization market is expected to jump from USD 3.51 billion in 2024 to an incredible USD 25.2 billion by 2035. This massive expansion is fueled by the non-stop demand for safer ways to pay online. You can dive deeper into these numbers and market trends in this detailed industry report.
The Real-World Security Benefits of Tokenization
Once you understand how payment tokenization works, its main purpose becomes crystal clear: it’s a powerful security shield for every single transaction. The biggest benefit is simple but incredibly effective—it dramatically shrinks the "attack surface" for cybercriminals. By swapping a valuable credit card number for a useless token, the data flowing through a merchant's systems becomes completely meaningless to thieves.
Think of it this way: a thief breaks into a museum to steal a priceless painting but finds only a numbered ticket in its place. That ticket is worthless outside the museum’s specific redemption system. A stolen token is the exact same concept. It's just a reference number, not the actual asset, which makes data breaches far less catastrophic for businesses and their customers.
Simplifying PCI DSS Compliance
A huge reason businesses adopt payment tokenization is to get a handle on PCI DSS compliance. The Payment Card Industry Data Security Standard (PCI DSS) is a strict set of rules for any company that touches cardholder data. Getting compliant can be a complex, expensive, and time-consuming headache. To get a better sense of what's involved, you can learn more about PCI Compliance for Shopify.
Tokenization makes this entire process much, much easier. Since the merchant’s systems no longer store or even process the sensitive Primary Account Numbers (PANs), the scope of their PCI DSS assessment shrinks dramatically.
By removing raw card data from your environment, you effectively sidestep many of the most demanding PCI DSS controls. This not only saves money on audits and security infrastructure but also frees up resources to focus on growing your business.
This isn't just a small convenience; it's a strategic move that lowers both your risk and your day-to-day operational costs. Tokenization also bolsters other security measures. Our guide on what is transaction monitoring explains how these different layers can work together to create an even stronger defense.
The Impact on Global Payments
The rapid adoption of this technology really speaks to how effective and important it is in today's economy. This growth isn't just a passing trend; it's a fundamental shift in how the world approaches payment security.
The numbers are staggering. By early 2025, Visa had already issued over 12.6 billion tokens globally. And Mastercard reported that by 2024, roughly one-third of all its global transactions used tokenization. This shows it has moved from a niche tool to a mainstream security standard, paving the way for safer and smoother payments everywhere.
At the end of the day, tokenization delivers a win-win. It gives customers peace of mind that their financial data is safe, while offering businesses a robust, scalable, and cost-effective way to secure transactions and build lasting trust.
Understanding Tokenization vs Encryption

When we talk about protecting payment data, two terms always come up: tokenization and encryption. They’re often used interchangeably, but they are fundamentally different tools for different jobs. Getting this difference right is crucial for building a truly secure payment system.
Let's clear it up with a quick analogy. Imagine you have a priceless family heirloom.
Encryption is like putting that heirloom into an unbreakable safe in your living room. The heirloom is still there, but it's scrambled behind a complex lock. Only someone with the correct key can open the safe and see the heirloom in its original form. If a burglar breaks in, they might get the safe, but they can't get what's inside. The valuable item is still on your property, just heavily disguised.
Tokenization, on the other hand, is like taking that heirloom to a professional, high-security vault far away. In return, the vault gives you a unique claim ticket. This ticket has no value on its own; it’s just a reference number. If a burglar steals the ticket from your house, it's useless to them. The actual heirloom is nowhere near your home, making a break-in far less risky.
Core Technical Differences
This analogy gets at the heart of the technical distinction. Encrypted data can always be reversed—or decrypted—back to its original state with the right key. A token, however, can't be mathematically reversed to figure out the original card number. It’s a stand-in, not a disguise.
The crucial takeaway is this: With encryption, the sensitive data is disguised. With tokenization, the sensitive data is replaced. This replacement is what makes tokenization so effective at reducing PCI DSS scope and minimizing the impact of a data breach.
To make it even clearer, let's put the two side-by-side.
Tokenization vs Encryption A Side-by-Side Comparison
This table highlights the fundamental differences between tokenization and encryption in the context of data security.
| Feature | Payment Tokenization | Encryption |
|---|---|---|
| Data Format | Creates a non-sensitive token that doesn't share the format of the original data. | Scrambles data into an unreadable format but maintains its original data type. |
| Data Storage | Moves the original data to a secure, centralized vault, removing it from local systems. | Keeps the altered (encrypted) data within your systems. |
| Reversibility | Irreversible. The token cannot be reverse-engineered to find the original data. | Reversible. Can be decrypted back to its original form using a cryptographic key. |
| Compliance | Significantly reduces PCI compliance scope by removing card data from your environment. | Reduces risk, but because the encrypted data is still present, systems remain in PCI scope. |
Ultimately, both have their place. Encryption is absolutely essential for protecting data as it travels across networks (data in transit). But for protecting stored payment information, tokenization is the superior choice.
It doesn’t just lock the data up; it takes the sensitive data out of your environment completely. For any business that handles customer payments, this offers a much stronger and more compliant security posture.
Where You See Payment Tokenization in Action

You might think payment tokenization is some complex, behind-the-scenes tech for bankers and developers. But the truth is, you probably use it every single day without even realizing it. It’s the invisible security guard that makes so many modern conveniences possible, from one-click checkouts to tapping your phone to pay.
Think about the classic "card on file" feature. When you save your credit card on a site like Amazon or your favorite online store, you’re not actually handing over your precious 16-digit number for them to lock away in a database. Instead, the merchant stores a unique, non-sensitive token that only works for purchases with them. If they ever have a data breach, the hackers get a useless string of characters, not your real card info.
Everyday Digital Commerce
This technology is the quiet engine powering a huge chunk of our digital lives, especially where speed and trust are critical.
In-App Purchases: That new game level you just bought or the subscription you started through your phone's app store? Tokenization made it happen. Your device used a secure token to complete the purchase, so the app developer never saw or handled your credit card details.
Recurring Billing: For services like Netflix, Spotify, or your gym membership, a payment token is used for those automatic monthly charges. This is a game-changer for businesses because they don't have to hold onto sensitive customer data. It’s also better for you—if your card expires, the token can often be updated automatically by the card network, so you don't have to deal with missed payments and service interruptions.
Tokenization transforms payments from a point of vulnerability into a seamless, trusted interaction. It’s the engine that allows convenience and top-tier security to coexist in our daily digital lives.
The Rise of Mobile Wallets
Mobile wallets are where tokenization really gets to shine. Services like Apple Pay, Google Pay, and Samsung Pay are built entirely on this secure foundation.
When you first add a credit card to your mobile wallet, the card network (like Visa or Mastercard) generates a completely separate, device-specific token. This is often called a Device Primary Account Number (DPAN), and it’s stored in a secure chip on your phone.
So when you tap your phone at the checkout counter, your device sends this DPAN to the terminal—not your actual card number. Your real account information stays safely tucked away on your device, completely shielded from the transaction.
And this isn't a niche feature anymore. The use of tokenization is exploding. In fact, projections show that network tokenized transactions could soar to 574 billion worldwide by 2029, thanks in large part to the convenience and security of mobile payments. If you want to dive deeper into the numbers, you can explore more about the future of tokenization in this Juniper Research report.
Choosing the Right Tokenization Solution
Picking a payment tokenization provider is more than just a tech choice—it's a critical business decision. The right partner can strengthen your security, elevate the customer experience, and ultimately protect your revenue. But not all solutions are built the same, so you need to look past the marketing and focus on what truly fits your business.
First things first: security. This is non-negotiable. Dig into a provider’s security credentials, starting with their PCI DSS validation. Your provider is essentially the guardian of your customers' most sensitive information, so there's absolutely no room for error here. Think of it as the foundation—if it’s not solid, nothing else matters.
Next up, how will this thing actually plug into your existing systems? This is where the technical details can make or break the project.
- API-Based Integration: This route gives you complete control to build a fully custom checkout experience. The trade-off? It demands significant developer time and expertise.
- Hosted Payment Fields: This is a much simpler path. It keeps sensitive card data entirely off your servers, which dramatically shrinks your PCI compliance workload.
The decision really boils down to how much control you need versus how much complexity you can handle.
Evaluating Different Tokenization Models
Beyond the initial setup, you'll find there are different ways tokenization can be structured. The biggest split is between what we call vaulted and vaultless tokenization.
A vaulted model is the classic setup. Your payment provider securely stores the original card data in their digital vault and hands you a token to use for future charges. This is perfect for businesses with recurring billing, subscriptions, or any "card-on-file" features.
On the other hand, a vaultless model doesn't rely on a central vault managed by your provider. Instead, it often involves network tokens generated by card brands like Visa and Mastercard. This can be a slicker process for certain types of transactions but might not offer the same kind of flexibility for every business.
Your choice of tokenization solution should align directly with your business model. A subscription service has very different needs from a one-off retail store, and your provider should support your growth, not hinder it.
Finally, don't forget about the future. Consider scalability and cost. Does the pricing make sense as you grow? A transparent fee structure is a must. A great partner will have the infrastructure to handle your busiest seasons without breaking a sweat, giving you the confidence to expand.
Got Questions About Tokenization? Let's Clear Things Up.
As we get to the end of our guide, a few common questions usually pop up. It's one thing to understand the theory, but it's another to see how it all plays out in the real world. Let's tackle some of the most frequent queries people have about payment tokenization.
Is Tokenization Completely Foolproof?
It’s tempting to look for a single piece of tech that can solve all security problems, but the truth is, no such thing exists. Tokenization is no exception. It is incredibly good at one specific, and very important, job: making stolen data useless. If a hacker breaks into a server and only gets a list of tokens, they've got nothing of value.
That said, tokenization won't protect against every type of fraud. For instance, it can't stop a phishing scam that tricks a customer into willingly authorizing a payment, nor can it prevent an account takeover where a fraudster gains control of a legitimate user's account. Think of it as a critical component in a wider security toolkit, not the entire defense system on its own.
Does Tokenization Slow Down the Checkout Process?
This is a big concern for anyone focused on user experience, but you can rest easy. The answer is a firm no. The magic of creating and swapping a token for real card data happens in the blink of an eye—literally milliseconds—and is completely invisible to the customer.
For the person buying from you, the checkout feels seamless and quick. In many cases, especially with one-click payments that rely on stored tokens, it's actually faster than a traditional checkout.
The complex, behind-the-scenes dance of token creation and validation is so finely tuned that it adds no noticeable lag to the transaction. You get all the security benefits without sacrificing a smooth customer journey.
Can One Token Be Used at Different Stores?
This really depends on what kind of token we're talking about. The most common type, a merchant-specific token, is locked down to the business that requested it. This is a deliberate security feature. If a token created for "The Corner Bookstore" is stolen, it’s completely worthless if someone tries to use it at "The Coffee Shop" next door.
Then you have network tokens. These are the ones issued by major card networks like Visa and Mastercard, often for use in mobile wallets like Apple Pay. These tokens are designed to work across any merchant that accepts that wallet, but they add their own security layer by being cryptographically tied to your specific device.
Ready to secure your transactions and simplify payments? BlockBee offers a robust, non-custodial crypto payment gateway that gives you full control over your funds. Explore our developer-friendly tools and start accepting crypto today.
