
What is Cold Storage Crypto? Secure Your Digital Assets Today
When we talk about crypto cold storage, we're talking about the digital equivalent of a high-security vault. It’s the practice of keeping your cryptocurrency private keys completely offline, far away from the reach of the internet. This method is widely considered the gold standard for long-term, secure crypto holding, offering the strongest protection against online hacking, malware, and digital theft.
Decoding Cold Storage and Its Importance

To really get your head around cold storage, let's use a real-world analogy. Think about your everyday money. You probably keep a bit of cash in your wallet for daily expenses—it's convenient and easy to get to. In the crypto world, this is what we call a "hot wallet." Hot wallets are software programs on your phone or computer that are always connected to the internet, which makes them perfect for frequent trading and quick payments.
But you wouldn't walk around with your life savings stuffed in your back pocket, would you? Of course not. You'd put the bulk of it in a secure bank vault. Cold storage serves the exact same purpose for your digital assets. It takes your private keys—the secret passcodes that give you control over your crypto—and locks them away from any online connection.
The whole idea is beautifully simple but incredibly effective: if a wallet is never connected to the internet, online hackers can't get to it. This "air-gapped" security measure cuts off the most common ways thieves try to steal digital currency.
The Growing Demand for Offline Security
This isn't just a paranoid niche, either. The demand for offline security is exploding. The global cold storage wallet market is already valued at around $1.63 billion, fueled by a growing understanding of online security risks. Retail investors have bumped up their cold wallet ownership by 34% in just a year, while institutions are moving even faster, with adoption growing by 51%. The message is clear: everyone is taking offline protection seriously. For more data, you can check out some interesting crypto wallet statistics on CoinLaw.io.
So, let's dive into how these offline solutions work, the different types you can use, and why they're so important. A great starting point is to see how they stack up against their online counterparts.
A Quick Look at Hot Wallets vs Cold Wallets
Before we get into the nitty-gritty of cold storage, this quick table breaks down the fundamental differences between the two main types of crypto wallets.
| Feature | Hot Wallet (Online) | Cold Wallet (Offline) |
|---|---|---|
| Internet Connection | Always connected to the internet. | Completely disconnected from the internet. |
| Security Level | Vulnerable to online threats like hacking. | Extremely high security; immune to online attacks. |
| Primary Use Case | Daily spending and frequent trading. | Long-term holding ("HODLing") of large amounts. |
| Convenience | Highly convenient and fast for transactions. | Less convenient; requires extra steps to transact. |
| Examples | Mobile apps, desktop software, exchange wallets. | Hardware devices (e.g., USB-like drives), paper wallets. |
As you can see, the choice between a hot or cold wallet really boils down to balancing convenience against security. For serious, long-term investors, the robust protection of a cold wallet is non-negotiable.
How Cold Storage Keeps Your Crypto Safe
To really get what cold storage is all about, you have to look at how it works on a mechanical level. The whole system hinges on one simple, unbreakable rule: protect your private key no matter what. This key is your digital signature—it's what authorizes every transaction and proves you actually own your crypto.
Think of it this way. Your public address is like your bank account number; you can give it to anyone so they can send you funds. Your private key, on the other hand, is like your secret PIN and password all rolled into one. If someone gets their hands on that key, they have total control over your money. It's game over.
The Offline Signing Process
The real magic of cold storage is that it generates and holds onto this "secret PIN" in a place that's completely cut off from the internet. A hardware wallet, for instance, is basically a small, specialized computer with a single purpose: to guard your private key and make sure it never, ever connects to the web. This creates what we call an "air gap"—a physical barrier between your key and any online dangers.
This entire setup ensures that even when you're making a transaction, your private key stays locked down and isolated.
This flow shows you the three main stages of a secure transaction using cold storage.
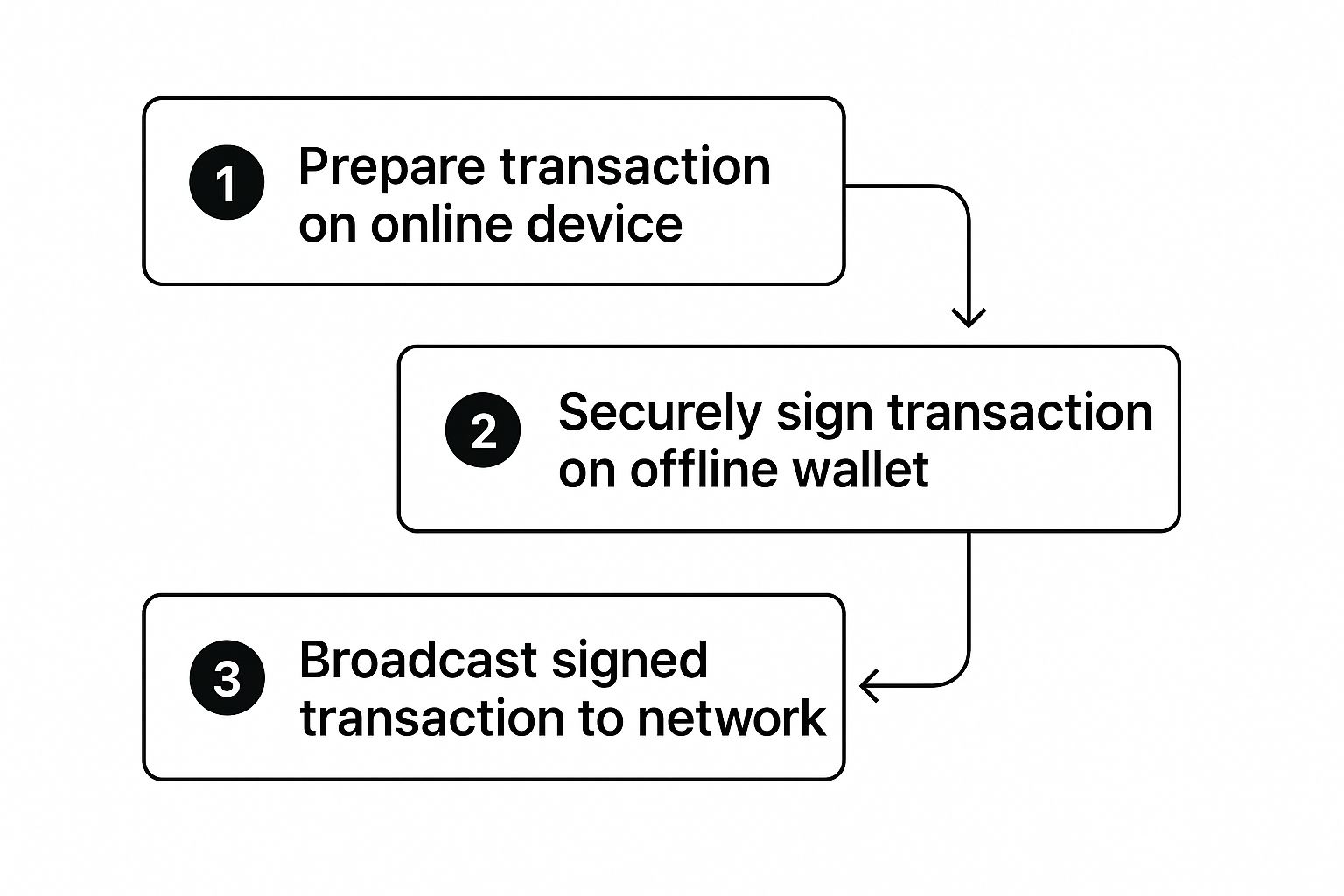
As you can see, the private key never leaves the offline device. That’s the entire foundation of cold storage security.
How A Transaction Actually Works
So, you might be wondering, "How can I spend my crypto if the keys are offline?" It’s a clever little dance between your online device (like your laptop or phone) and your offline cold wallet.
Here’s how it unfolds, step by step:
Prep the Transaction: You kick things off on your internet-connected device, using a software wallet interface. You’ll enter the recipient’s address and the amount you want to send. The software then pieces together an unsigned transaction. Picture it as a check you’ve filled out but haven't signed yet.
Sign It Offline: Next, this unsigned transaction data is passed over to your hardware wallet (usually through a USB cable or Bluetooth). Inside the wallet's secure chip, the device uses your private key to cryptographically "sign" the transaction, proving it came from you. And here's the crucial part: the private key itself never, ever leaves the hardware wallet.
Broadcast the Signed Transaction: The wallet sends only the signed transaction back to your computer. This is now a valid, authorized instruction. Your computer then pushes this signed transaction out to the cryptocurrency network to be confirmed and added to the blockchain.
This method lets you interact with the blockchain without ever putting your most valuable secret at risk. For a much deeper look into why this digital key is so critical, check out our guide on private key security.
The Air-Gapped Advantage
This air-gapped design makes your crypto assets virtually bulletproof against the most common types of theft, like remote hacking, phishing attacks, and malware. A virus on your computer might see the transaction you're putting together, but it can't forge your signature because it has no way to access the private key tucked away safely in your hardware wallet.
The core security benefit is beautifully simple: an online attacker cannot steal what they cannot reach. By physically isolating the private key, cold storage closes the main door that hackers use to steal digital assets.
Of course, the device itself is only half the battle. Truly keeping your crypto safe in cold storage means putting a robust encryption key management policy in place. This set of rules governs how your keys are created, stored, and used, ensuring they’re handled with maximum security from start to finish. It’s the perfect complement to the physical protection your wallet provides.
Exploring The Main Types Of Cold Storage Wallets

So, you get the big picture of cold storage. Now comes the important part: picking the right method to lock down your assets. Not all offline solutions are created equal, and the two you’ll run into most often are hardware wallets and paper wallets.
Each one has its own personality, with a unique set of pros and cons. Think of it as choosing between a high-tech digital vault and a classic, old-school safe deposit box. Understanding the trade-offs is key to building a security strategy that actually works for you.
Hardware Wallets The Modern Fortress
Imagine a specialized USB stick, built like a miniature fortress with one purpose: to guard your private keys. That's a hardware wallet in a nutshell. These physical gadgets generate and store your keys in a completely isolated, offline chip, far away from the prying eyes of the internet.
They are engineered from the ground up for maximum security. Most come packed with features like:
- Secure Chips: These are special, tamper-resistant microcontrollers that act as a black box for your keys, shielding them from both software hacks and physical tampering.
- Physical Buttons: To send any funds, you have to physically press buttons on the device itself. This simple step is a powerful defense, stopping malware from draining your account even if your computer is completely infected.
- Recovery Seed Phrase: When you first set it up, the wallet gives you a secret recovery phrase (usually 12 or 24 words). This is your ultimate backup—if your device is ever lost, stolen, or smashed, you can use this phrase to get all your funds back on a new one.
This powerful combination makes hardware wallets the go-to choice for anyone serious about securing a significant amount of crypto. To get a much deeper look, you can learn more about what a hardware wallet is in our dedicated guide.
Paper Wallets The Original Offline Method
Long before fancy hardware devices hit the scene, paper wallets were the original cold storage solution. And they are exactly what they sound like: a piece of paper with your public and private keys printed on it, often as QR codes you can scan.
The process is simple. You use an offline tool to generate a new key pair, print it out, and then stash that paper somewhere incredibly safe—like a fireproof safe or a bank vault. By doing this, you ensure your private key never even touches an internet-connected device.
A paper wallet is the ultimate low-tech security solution. Its strength comes from physical security, not digital encryption, making it immune to hardware failures, malware, or firmware bugs. On the flip side, it's completely defenseless against physical threats like fire, floods, or just being accidentally tossed in the trash.
A Detailed Comparison of Storage Options
The decision between a hardware and paper wallet really boils down to balancing security, convenience, and durability. The global crypto wallet market, valued at around USD 12.59 billion, is expected to skyrocket to over USD 100.77 billion—a trend largely driven by the growing demand for the superior security that cold wallets provide.
To help you figure out what's best for you, let’s put them head-to-head.
Hardware Wallets vs Paper Wallets a Detailed Comparison
Here’s a direct comparison breaking down the advantages and disadvantages of the two most common cold storage methods. This should help you choose the right option for your security needs.
| Aspect | Hardware Wallets | Paper Wallets |
|---|---|---|
| Security Features | Excellent. You get a secure chip, PIN protection, physical transaction confirmation, and robust encryption. | Good, but basic. Security depends entirely on keeping the paper physically safe. It's toast if the key is ever exposed. |
| Ease of Use | Pretty user-friendly. They're designed for regular use with apps that make transactions secure and simple. | Difficult for newcomers. To spend funds, you have to "sweep" keys into a hot wallet, a technical process that kills the security. |
| Durability | Generally durable, but they're still electronics. They can be damaged by water, impact, or electronic failure. | Extremely fragile. It's just paper, so it's vulnerable to fire, water, faded ink, and tearing. Easily lost or destroyed. |
| Recovery Options | Strong. Your recovery seed phrase is a lifeline, letting you restore everything on a new device. | None. If you lose the paper, your funds are gone forever. Period. There is no backup system. |
| Cost | An upfront investment, typically $50 to over $200 depending on the model and its features. | Basically free, aside from the ink and paper. It's a very accessible option if you're just starting out. |
When it comes down to it, a hardware wallet offers the best all-around package of top-tier security and real-world usability for most people. While a paper wallet is a simple and free way to get your funds offline, its fragility and the all-or-nothing risk of having no backup make it a much dicier choice for holding crypto long-term.
Why Cold Storage Is Your Best Defense
Think of cold storage as building a digital Fort Knox for your crypto. It’s not just about picking a piece of tech; it’s a deliberate strategy to put your assets completely out of reach from online threats. The main advantage here is creating what’s called an “air gap”—a physical separation between your private keys and the internet.
This gap is what makes cold storage so powerful. Malware, phishing attacks, and keyloggers that plague online wallets simply can't jump across a physical divide. It’s like a hacker trying to break into a bank vault from their laptop on another continent. It just isn't happening. This is the core security promise of cold storage.
You Are in Complete Control—True Self-Custody
One of the biggest wins with cold storage is achieving true self-custody. When you leave your crypto on an exchange, you’re essentially trusting them with your money, just like a traditional bank. But this introduces a huge risk: what if the exchange gets hacked, goes bust, or decides to freeze your account? Your funds are stuck.
Cold storage completely flips that script. You hold the keys.
By taking your assets offline, you cut out the middleman. You become your own bank, holding the final say over every single transaction. It all comes back to a core crypto principle: "not your keys, not your coins."
This move towards self-sovereignty is a massive driver of growth in the space. The market for cold storage wallets, valued around USD 3.5 billion, is expected to skyrocket past USD 10.7 billion as more people realize the importance of direct control. This isn't just a niche trend; it's a fundamental shift in how people secure their digital wealth. You can dive deeper into these numbers and learn more about the crypto cold storage market to see the full picture.
The Ultimate Fail-Safe: Physical Confirmation
Hardware wallets take security a step further with a brilliant, low-tech feature: physical transaction confirmation. Let’s say the worst happens and your computer is riddled with malware. Even then, a hacker can’t touch your funds without you physically doing something.
Here's how it plays out in the real world:
- A scammer uses a virus to take over your machine and tries to send all your crypto to their own wallet.
- The transaction details are automatically sent to your connected hardware wallet for approval.
- To actually sign and send the transaction, you have to physically press a button on the device.
Since you obviously didn't start this transfer, you’d just hit "reject" on the wallet's little screen. The transaction fails, and your funds are safe. This physical step is the final checkpoint, making it virtually impossible for anyone to move your assets without your direct, in-person consent. It’s this blend of offline keys and a required physical action that makes cold storage such a rock-solid defense.
Understanding and Mitigating Cold Storage Risks

While cold storage is fantastic at shielding your crypto from online hackers, it brings a whole new set of worries into the physical world. Suddenly, you're not thinking about malware or phishing scams. Instead, you're concerned with real-world problems like theft, loss, and damage.
When you move your assets offline, you essentially become your own bank. That’s incredibly empowering, but it also means there’s no customer service line to call if you lose your wallet or forget your password. The buck stops with you.
It's crucial to understand the concept of a "single point of failure"—and in this case, it’s your recovery seed phrase. If your hardware wallet is lost or destroyed and you don't have this phrase, your crypto is gone forever. No recovery questions, no password reset. The funds are simply inaccessible.
The Most Common Physical Threats
Unlike sneaky digital attacks, physical threats are usually pretty blunt and can be just as devastating. Protecting your cold storage setup means having a solid plan for these tangible dangers.
Here’s what you really need to watch out for:
- Physical Loss: Hardware wallets are tiny and can easily get misplaced. A paper wallet can be mistaken for a random piece of paper and tossed in the trash.
- Theft: If someone gets their hands on your device and your PIN, they can access your funds. Worse, if they find just the seed phrase, they have everything they need.
- Accidental Damage: Think about a house fire, a flood, or even just a spilled coffee. Any of these could easily destroy a paper wallet or fry the electronics in a hardware device.
Each of these scenarios makes one thing crystal clear: relying on a single device or one copy of your recovery phrase is a massive gamble. A smart security plan is all about building in redundancy.
Protecting Your Ultimate Backup: The Recovery Seed Phrase
Your hardware device can be replaced. Your recovery seed phrase cannot. Guarding this sequence of words is, without a doubt, the single most important part of securing your crypto. If it gets into the wrong hands, a thief can clone your wallet and drain your accounts without ever needing your physical device.
The good news is there are time-tested ways to keep this master key safe. First and foremost, never, ever store your seed phrase digitally—not on your computer, not on your phone, not in the cloud. Doing so completely defeats the purpose of cold storage. Your focus should be on creating tough, redundant physical backups.
Here are a few of the most effective strategies:
- Use a Steel Plate: Etch or stamp your seed phrase onto a metal plate. This makes it resistant to fire, water damage, and corrosion. It’s a huge step up from a flimsy piece of paper.
- Split the Phrase: This is a more advanced technique where you split your seed phrase into multiple parts and store each piece in a different, secure location. For instance, you could keep the first half in a safe deposit box and the other half with a trusted family member. An attacker would need to find all the pieces to do any damage.
- Create Multiple Backups: Don't stop at one copy. Make at least two or three physical backups of your seed phrase and keep them in different geographic locations. This way, if a fire or theft compromises one location, you're not out of luck.
Putting together a solid plan for secure seed phrase storage is non-negotiable. This is what truly separates a secure setup from one that’s only half-protected. By thinking ahead and guarding against these physical risks, you can ensure your assets are safe from every angle, giving you real peace of mind.
How Businesses Use Cold Storage for Secure Payments
Cold storage isn't just for the solo crypto investor hoarding Bitcoin in a safe. It's a fundamental security practice for any business that accepts or holds digital assets. If your company handles crypto payments daily, you're constantly walking a tightrope between needing funds ready to go and keeping your corporate treasury safe.
The answer is a surprisingly simple, two-wallet system. It's all about balancing accessibility with Fort Knox-level security.
This strategy pairs a day-to-day hot wallet with a main cold storage vault. The best way to think about it is like a retail store's cash register. The register (your hot wallet) has enough cash to handle daily customer transactions, but you wouldn't keep the entire business's savings in it overnight. That's what the safe in the back office—your cold storage—is for.
The Sweep and Secure Workflow
The magic of this system lies in a simple, repeatable process: regularly "sweeping" funds from your operational hot wallet into your offline cold storage. It's a routine that dramatically cuts down on the amount of money you have exposed to online threats at any single moment.
Most businesses set a clear threshold for this. For instance, you might decide that any time your hot wallet's balance creeps over $10,000, the excess gets moved to the cold wallet. This little piece of financial hygiene ensures the vast majority of your company's crypto is safely offline and out of reach of hackers, all without disrupting your daily payment flow.
Adopting this hybrid model gives you the best of both worlds:
- Minimized Exposure: Your core assets are tucked away in cold storage, insulated from online attacks.
- Operational Fluidity: The hot wallet stays topped up just enough to process payments through gateways like BlockBee without a hitch.
- Reduced Risk: In a worst-case scenario where the hot wallet is compromised, the loss is capped to the relatively small amount needed for daily business.
Strengthening Internal Controls with Multi-Signature Protocols
A smart wallet setup is only half the battle; you also need iron-clad internal rules. One of the most powerful tools for this is a multi-signature (multisig) requirement for any transaction moving out of your main cold storage.
In simple terms, this means a transfer requires sign-off from several key people in your company—not just one.
Think of a multisig wallet as needing two or more keys to open a bank's vault. No single person has total control, which is a powerful safeguard against both external hacks and the potential for internal mistakes or fraud.
By combining a disciplined sweep-and-secure routine with robust controls like multisig, any business can step into the world of crypto payments with confidence. You get all the convenience of a hot wallet for your customers, backed by the impenetrable security of cold storage protecting your company’s bottom line.
Common Questions About Crypto Cold Storage
Even after getting the hang of how cold storage works, a few key questions always seem to pop up. Let's tackle some of the most common ones to clear up any lingering confusion you might have about taking your crypto offline.
Can Crypto Be Stolen from Cold Storage?
While cold storage makes you practically immune to online hacks, your crypto isn't 100% invincible. The threat simply moves from the digital world to the physical one. If a thief got their hands on your hardware wallet and managed to guess your PIN, they could theoretically access your funds.
But the real weak spot isn't the device itself—it's your recovery seed phrase. If someone finds that list of words, they can clone your entire wallet on a brand-new device and drain every asset you have. They wouldn't even need your original hardware. This is why protecting your seed phrase is even more critical than hiding the device.
Think of it this way: Your hardware wallet is a sturdy gate, but your recovery phrase is the master key to the entire fortress. Guarding it is the most important job you have.
What Happens If My Hardware Wallet Is Lost or Broken?
This is a huge fear for many, but the answer is reassuring. As long as you have your recovery seed phrase, your crypto is completely safe. Remember, your funds don't actually live on the device; they live on the blockchain. The wallet is just a secure key for accessing them.
If your device gets lost, stolen, or just stops working, getting back in is simple:
- Get a New Wallet: Buy a new hardware wallet. It can be the same brand or another compatible one.
- Start the Recovery: When setting up the new device, you'll see an option to "restore" or "recover" a wallet. Choose it.
- Enter Your Seed Phrase: Carefully type in the 12 or 24 words from your recovery phrase in the correct order.
And that's it. The new device will sync with the blockchain and give you full access to all your cryptocurrency, exactly as you left it.
How Often Should I Move Funds to Cold Storage?
There’s no magic number here; it really depends on how you use your crypto and your personal comfort level with risk. The best approach is to have a system.
For a business that handles daily transactions, a great strategy is to set a balance limit on your hot wallet. For example, you might decide that any time the hot wallet balance climbs above $5,000, you "sweep" the excess into your cold storage vault. This keeps enough funds accessible for operations while locking away the majority from online threats.
For individuals, a good rule of thumb is to move funds after any large purchase or whenever the amount in your hot wallet grows beyond what you’d be comfortable losing. Of course, secure storage is just one piece of the puzzle; a deeper dive into general crypto trading concepts can also help you manage your assets more effectively.
At BlockBee, we specialize in helping businesses set up these kinds of hybrid systems—combining the flexibility of hot wallets for payments with the rock-solid security of cold storage for your main reserves. Discover how our non-custodial payment platform can secure your business's crypto operations.
