
Understanding symmetric and asymmetric encryption: A quick guide
At their core, the difference between symmetric and asymmetric encryption all comes down to the keys. Symmetric encryption uses a single, shared key to both lock (encrypt) and unlock (decrypt) information. In contrast, asymmetric encryption uses a pair of keys—one public and one private. This fundamental distinction is what shapes their speed, security, and how we use them to protect our digital lives.
The Foundation of Modern Data Security
Think of it like this: imagine you have a secret diary. To keep it safe, you use a special lock that only one unique key can open. That’s symmetric encryption in a nutshell. The same key that locks the diary is the one needed to unlock it. It's wonderfully simple and fast, but it presents a tricky problem: how do you safely share that key with someone you trust without a third party getting their hands on it first?
Now, let's try another analogy. Picture a secure mailbox with a slot. Anyone can drop a letter into the slot (that’s your public key), but only you have the special key to open the box and read what's inside (that’s your private key). This is the clever solution that asymmetric encryption provides. It solves the key-sharing dilemma, enabling secure communication between two people who may have never met before.
Why Both Encryption Methods Matter
These two approaches are the cornerstones of digital trust. They don't compete; they work together. Most of the secure systems you interact with every day—from browsing a website with HTTPS to making a payment online—use a hybrid model that blends the strengths of both. This tag-team approach delivers both rock-solid security and the performance needed for a smooth experience.
The importance of this technology is booming. The global data encryption market was valued at USD 16.8 billion in 2025 and is projected to soar to USD 65.5 billion by 2034, largely thanks to the rise of cloud computing and a greater focus on cybersecurity.

The image above captures the essence of digital trust, where sophisticated keys protect our most valuable information. Understanding how to manage these systems is critical, especially in complex environments. For anyone looking to get a better handle on today's security challenges, exploring strategies for mitigating cloud computing security risks is a great next step.
How Symmetric Encryption Uses a Shared Secret
Think of a high-security safe where you keep important documents. This safe has a single, unique key. You turn it one way to lock it, and you use that very same key, turned the other way, to get your documents back out. That’s the core idea behind symmetric encryption. It’s built on a simple yet powerful principle: one shared key locks (encrypts) and unlocks (decrypts) the data.
This "shared secret" approach makes the whole process incredibly efficient. For it to work, both the sender and the receiver have to have the exact same key. When you want to send a protected message, you use that key and a specific algorithm to scramble your plain text into unreadable ciphertext. The recipient then uses their identical key to reverse the process, turning the gibberish back into your original message.
The biggest win here is speed. Because it’s just one key and the math involved is less complex than other methods, symmetric encryption can chew through huge amounts of data in no time. This makes it the perfect tool for jobs that need high performance without compromising on security.

The Powerhouse Algorithms Behind the Scenes
While the concept is straightforward, the technology is anything but. Several battle-tested algorithms drive symmetric encryption, but one, in particular, has become the industry gold standard: the Advanced Encryption Standard (AES). It was adopted by the U.S. government and is now used globally, known for its potent blend of speed and security. AES works by breaking data into fixed-size blocks and then running them through multiple rounds of complex mathematical transformations, making the final ciphertext incredibly tough to crack.
The real strength of AES lies in its key length options—128, 192, or 256 bits. For perspective, an attacker trying to brute-force a 256-bit key would have to try a number of combinations so astronomically large that it’s considered impossible with today's computers.
You might hear about other symmetric algorithms like Blowfish or Twofish, but AES is the default choice for nearly all modern applications. It’s not just proven and secure; it’s also built into most modern processors for hardware-accelerated speed.
When Speed and Efficiency Are Critical
The high-speed performance of symmetric encryption makes it a natural fit for data-heavy tasks. It can secure massive volumes of information without grinding systems to a halt, which is why it has long been the dominant force in the global data encryption market.
In fact, the symmetric encryption segment accounted for a staggering 61.3% of the total market revenue, making it the most popular method by a long shot. Its dominance comes directly from its ability to handle bulk data protection, a crucial need for everything from cloud storage to internal company networks. You can explore more data encryption market trends to see just how widespread its impact is.
Here’s where you’ll find symmetric encryption working hard in the real world:
- Full-Disk Encryption: That padlock on your hard drive? Tools like BitLocker for Windows and FileVault for macOS use symmetric encryption to protect everything.
- Database Encryption: It’s used to lock down entire databases or just specific columns containing sensitive information, like customer payment details.
- Large File Transfers: When you need to encrypt huge files or backups before uploading them to the cloud or sending them across a network, symmetric is the way to go.
But for all its strengths, the shared secret model has one major catch. If you and a colleague need to exchange encrypted files, how do you get the key to them securely in the first place? If you just email it, an eavesdropper could intercept it, and your entire security system falls apart. This “key distribution problem” is the fundamental weakness that led to the development of its counterpart: asymmetric encryption.
Understanding Asymmetric Encryption's Key Pair
While symmetric encryption is a workhorse for sheer speed, it has one major headache: the "key distribution problem." Think about it—how do you securely get that single, shared key over to the other person without someone snooping on it? Asymmetric encryption, also known as public-key cryptography, was born from the need to solve this exact puzzle.
Let's use an analogy. Imagine you have a special mailbox with a mail slot. Anyone can walk up and drop a letter in that slot—your friends, the mail carrier, anyone. That open slot is your public key. You can tell the whole world where your mailbox is, and it doesn't matter because all they can do is put things in.
But to actually open the mailbox and read the letters? You need a special, physical key that only you have. That’s your private key. You keep it secret, you never share it, and it guarantees that you're the only one who can access what's inside. This clever pairing of a public and private key is the magic behind asymmetric encryption.
The Dynamic Duo: Public and Private Keys
In an asymmetric system, the two keys are a matched set. They are mathematically tied together, but they are not the same. What one key locks, only its partner key can unlock. This creates a one-way security function that completely sidesteps the key-sharing dilemma.
You don't need a secret handshake or a secure courier to exchange keys anymore. You can shout your public key from the rooftops—post it on your website, add it to your email signature, whatever you want. There’s no risk because its only job is to lock things up, not open them.
This very mechanism is what allows two people who've never met to start a secure conversation over an insecure network like the internet. Someone uses your public key to scramble a message, feeling completely confident that only your private key can unscramble it.
Key Takeaway: The real power of asymmetric encryption comes from splitting the job of encryption and decryption. The public key is for locking, and the private key is for unlocking. You never have to share the secret key that does the unlocking.
Common Asymmetric Algorithms and Their Roles
Just like with symmetric methods, a few core algorithms do the heavy lifting for asymmetric encryption. You don't need to be a mathematician to use them, but it’s helpful to know the names. The two most common ones you'll run into are:
- RSA (Rivest–Shamir–Adleman): For a long time, RSA has been the gold standard for secure data transmission and digital signatures. It gets its strength from the fact that it’s incredibly difficult to figure out the two large prime numbers that were multiplied together to create the key. It's a cornerstone of protocols like TLS/SSL.
- Elliptic Curve Cryptography (ECC): ECC is the newer, more efficient kid on the block. It offers the same level of security as RSA but with much smaller keys. This makes it faster and a perfect fit for devices with less computing power, like your smartphone.
The trade-off for all this security and convenience? Speed. The math behind asymmetric encryption is much more complex than its symmetric counterpart, making it noticeably slower. For that reason, you wouldn't want to use it to encrypt a huge file directly.
Where Asymmetric Encryption Truly Shines
Because it's not the fastest tool in the shed, asymmetric encryption is reserved for specific jobs where trust and verification are everything.
It excels in these areas:
- Secure Key Exchange: This is its most popular gig. It’s used to safely wrap up and send a symmetric key to someone. Once they have it, they can use that faster key to encrypt the rest of the conversation.
- Digital Signatures: By "signing" a document with your private key, you create a digital fingerprint. Anyone with your public key can check that signature to prove it came from you and hasn't been tampered with.
- Authentication: It's used to prove identities online, making sure you’re actually talking to your bank's server and not an impostor.
The private key is the heart of this entire system. Protecting it is everything. If it gets compromised, the whole system of trust falls apart. To learn more about keeping it safe, be sure to read our guide on private key security.
A Head-to-Head Encryption Comparison
Deciding between symmetric and asymmetric encryption isn’t about crowning a champion. Think of them as different tools in a toolbox, each perfectly designed for a specific job. One gives you incredible speed, while the other offers an ironclad way to prove who you are.
To build a truly secure system, you need to understand precisely where each one shines. Let’s compare them on the factors that really matter, from how they manage keys to the horsepower they need to run.
Key Management and Complexity
The biggest split between these two methods comes down to key management. Symmetric encryption relies on a single, shared secret key. It's wonderfully simple on the surface, but the complexity explodes as you add more people to the circle of trust. How do you get the key to everyone securely? If just one person’s key is compromised, the whole system is at risk.
Asymmetric encryption neatly sidesteps this entire problem with its public-private key pair. You can post your public key on a billboard for the world to see, and it doesn't matter. It can only be used to encrypt data meant for you. The only thing that can unlock it is your private key, which you keep guarded. This design makes it incredibly easy and safe to start a secure conversation with anyone, anywhere.
Performance and Speed
When it's a race against the clock, there's no competition. Symmetric encryption is monumentally faster. The math behind it is much simpler, which means it can chew through huge amounts of data without breaking a sweat. This makes it the go-to choice for any heavy-lifting data protection tasks.
To put it in perspective, a symmetric algorithm like AES can be up to 1,000 times faster than an asymmetric one like RSA. This is exactly why you'd never use asymmetric encryption to, say, lock down an entire hard drive—it would take an eternity.
Asymmetric encryption is slow by design. Its complex, resource-hungry calculations are what make it so secure, but they also create a performance bottleneck. Its job isn't to encrypt massive datasets, but to handle critical, brief moments where establishing trust is everything.
Security Strengths and Ideal Use Cases
Each encryption method brings a unique set of security benefits to the table. Symmetric encryption's strength is confidentiality at scale. It’s brilliant for protecting data that's just sitting there, like files on a server or records in a database. Its whole purpose is to keep massive amounts of information unreadable to anyone without the shared key.
On the flip side, asymmetric encryption's strengths are authentication, integrity, and non-repudiation. It's how you verify you’re talking to the right person, not an imposter. It's also how you create digital signatures, which serve as a tamper-proof seal, proving a message is authentic and unaltered. This is absolutely essential for building trust on open networks like the internet.
This difference is also at the heart of modern financial security. For example, understanding key management is crucial in systems designed to protect sensitive payment data. You can see a real-world application of this concept by learning what is payment tokenization and how it secures transactions.
To make these differences crystal clear, here’s a detailed breakdown.
Detailed Feature Breakdown Symmetric vs Asymmetric Encryption
The table below provides a side-by-side summary of the most critical distinctions between these two powerful encryption methods.
| Attribute | Symmetric Encryption (e.g., AES) | Asymmetric Encryption (e.g., RSA) |
|---|---|---|
| Number of Keys | One single shared key for both locking and unlocking data. | A pair of keys: one public (for locking) and one private (for unlocking). |
| Performance | Very fast and efficient, ideal for encrypting large files and data streams. | Significantly slower due to complex mathematical computations. |
| Key Management | The main challenge is securely distributing and managing the shared key. | Solves the key distribution problem, as the public key can be shared openly. |
| Primary Use | Securing bulk data (e.g., full-disk encryption, database encryption). | Secure key exchange, digital signatures, and user authentication. |
As you can see, their operational profiles are almost mirror opposites. This is why they aren't competitors; they are partners. The most robust security systems use them together, which we'll explore next.
How Hybrid Encryption Secures the Modern Web
Symmetric and asymmetric encryption aren't rivals; they're more like partners in a highly effective security strategy. One offers lightning-fast speed, while the other provides rock-solid trust. The real magic, though, happens when you combine them. This powerhouse combination, known as hybrid encryption, is the engine running quietly behind almost every secure thing you do online.
Think of it like this: you need to send a heavy, locked treasure chest to a friend. You wouldn't ship the chest with the key taped to the outside, right? That’s far too risky.
Instead, you first send the small, lightweight key inside a virtually uncrackable puzzle box. This is your asymmetric encryption. Once your friend receives and solves the puzzle to get the key, you can safely ship the main treasure chest. Now they can easily unlock it. This is your symmetric encryption.
This "best of both worlds" approach uses the slow but super-secure asymmetric process for just one tiny, critical job: agreeing on a shared secret key. Once that's handled, everything switches over to the blazing-fast symmetric process to protect the actual data.
The TLS Handshake in Action
This hybrid model is what powers the TLS/SSL protocol—the very technology that puts that little padlock icon in your browser's address bar. Every time you connect to a secure website, a rapid-fire negotiation called the "TLS handshake" kicks off behind the scenes.
Here's a quick look at how it works:
- Your Browser Says Hello: Your browser reaches out to the website's server, asking for its public key and SSL certificate to make sure it's legit.
- The Server Proves Its Identity: The server responds, sending back its public key and a certificate signed by a trusted authority (like Let's Encrypt). This is its digital ID.
- Creating a Shared Secret: Your browser generates a brand new, temporary symmetric key, often called a "session key." It then locks this new key using the server's public key.
- Secure Key Exchange: The browser sends this encrypted session key back to the server. Since it was locked with the public key, only the server's matching private key can open it.
- Switching to Symmetric: Boom. Both your browser and the server now hold the exact same secret session key. They immediately switch to a fast symmetric algorithm (like AES) to secure all the data sent back and forth for the rest of your visit.
This whole exchange takes mere milliseconds, but it creates an incredibly secure private channel. Asymmetric encryption handles the initial introduction, and the much speedier symmetric encryption takes over for the main conversation.
The infographic below really clarifies the trade-offs and shows why this hybrid approach is so smart.
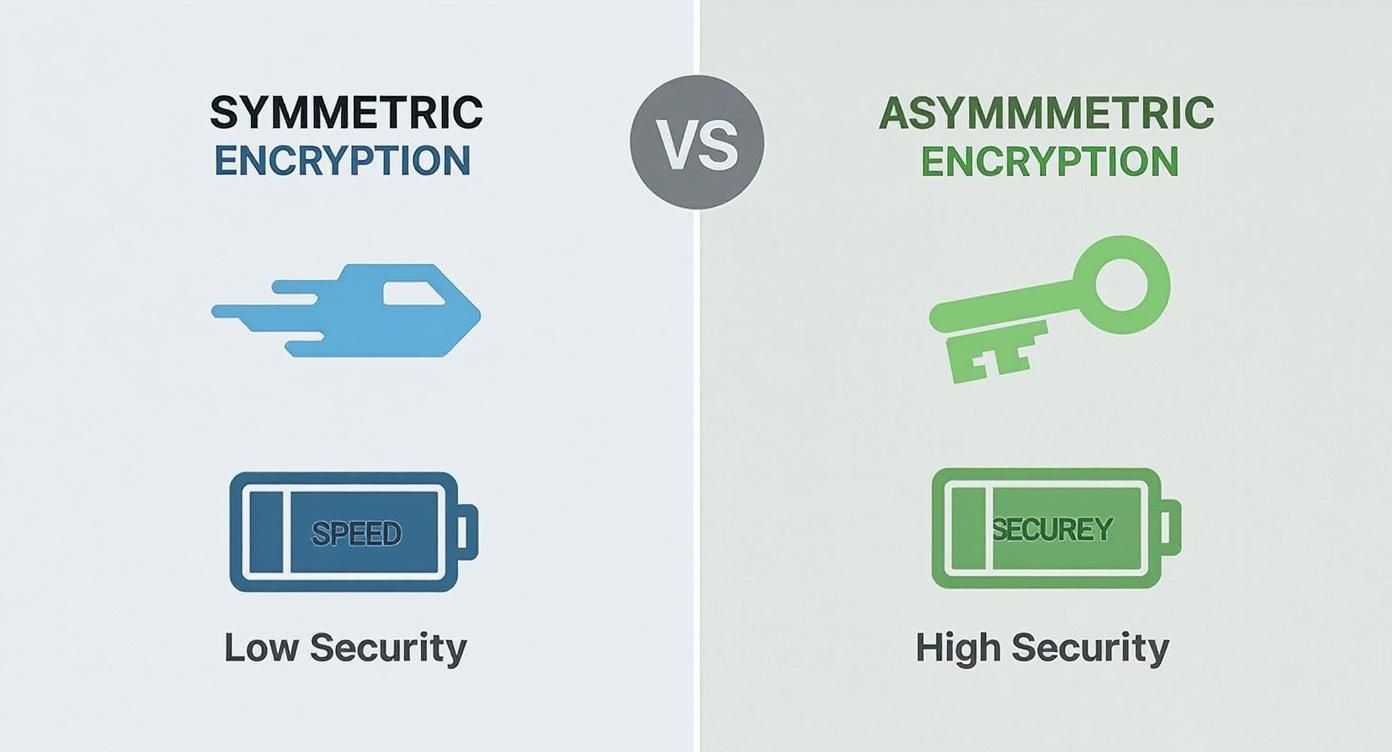
As you can see, one excels at speed while the other provides a secure way to establish trust, making them perfect partners.
Beyond Web Browsing
The power of hybrid encryption goes way beyond just websites. It’s the foundational tech for countless applications where both security and performance are non-negotiable.
Key Insight: The hybrid model solves the fundamental dilemma of online security: how can two parties who've never met establish a trusted, private line of communication over an open, untrusted network like the internet?
A great real-world example is a Virtual Private Network (VPN). VPNs use these exact principles to wrap your internet traffic in an encrypted tunnel, shielding your data from prying eyes.
Other common uses include:
- Secure Messaging Apps: End-to-end encrypted apps rely on this model to ensure only the sender and receiver can ever read the messages.
- Email Encryption: Protocols like PGP and S/MIME use a recipient's public key to lock down a message that only their private key can unlock.
- Secure File Transfers (SFTP): This system secures both the login process and the actual bulk data transfer, protecting files in transit.
This elegant combination of symmetric and asymmetric encryption is truly the unsung hero of our digital lives, providing a robust and efficient framework for trust and privacy all across the internet.
Common Questions About Encryption
Even after getting the hang of the basics, a few practical questions always pop up when you start working with symmetric and asymmetric encryption. Let's tackle some of the most common ones head-on to clear up any lingering confusion.
Why Not Just Use Asymmetric Encryption for Everything?
If asymmetric encryption is the gold standard for secure key exchange, why not use it for all our encryption needs? The short answer: it’s incredibly slow.
The complex math that makes asymmetric encryption so secure also makes it a massive resource hog. Think of it this way: asymmetric encryption is like an armored truck with a full security detail. It’s perfect for moving one priceless item—the key—safely, but it’s far too slow and expensive to move a whole warehouse full of goods.
Symmetric encryption, on the other hand, is the high-speed freight train. It’s built to carry the actual cargo—your data—quickly and efficiently.
Trying to encrypt large files or a continuous data stream with an asymmetric algorithm would bring most systems to a crawl. In fact, a symmetric algorithm like AES can be up to 1,000 times faster than an asymmetric one like RSA. That’s why the best systems use a hybrid approach, letting each type do what it does best.
Which Method Is More Secure?
This question comes up a lot, but it's a bit like asking if a sledgehammer is a better tool than a scalpel. It really depends on the job you're doing. When implemented correctly with modern algorithms and strong keys, both symmetric and asymmetric encryption are exceptionally secure.
The real measure of an encryption system’s security isn’t just the algorithm. It's a combination of the algorithm's strength, the length of the key, and, most critically, how well you protect that key.
A system using the strongest AES-256 symmetric encryption is completely useless if the shared key is written on a sticky note and left on a monitor. Likewise, an RSA asymmetric system falls apart the moment the private key is stolen.
Security is all about context:
- For encrypting large amounts of data at rest or in transit, a well-managed symmetric system offers unbeatable security and performance.
- For proving identity and securely exchanging keys, asymmetric encryption provides a level of trust and verification that symmetric methods simply can't.
Ultimately, the most secure systems don’t choose one over the other—they use both, working together.
What Happens If a Private Key Is Lost or Stolen?
Losing a private key is a five-alarm fire in the world of security. Since it's the one and only thing that can unlock data encrypted with its public partner, its loss or theft shatters the entire trust model of asymmetric encryption.
You're looking at two nightmare scenarios:
- If a private key is lost forever: Any data encrypted with the corresponding public key is gone for good. It's like losing the only key to a bank vault—the contents are still in there, but you're never getting them back.
- If a private key is stolen: An attacker can now decrypt any messages sent to you. Even worse, they can impersonate you by using your stolen key to create digital signatures, letting them authorize fraudulent transactions or sign malicious code in your name.
This is why protecting private keys is so incredibly important. For anyone dealing with high-value assets like cryptocurrency, rock-solid key protection is non-negotiable. One of the best defenses is understanding what a hardware wallet is and how it works, as these devices are designed from the ground up to keep private keys completely isolated from online threats.
Is AES a Symmetric or Asymmetric Algorithm?
AES, which stands for Advanced Encryption Standard, is a symmetric encryption algorithm. This means it uses a single key to both lock (encrypt) and unlock (decrypt) data.
It operates on 128-bit blocks of data and comes in three flavors based on key length: 128, 192, and 256 bits. Thanks to its incredible security and efficiency, AES has become the global standard. It's the workhorse algorithm quietly protecting everything from the files on your laptop to data in massive corporate databases.
How Do Digital Signatures Work?
A digital signature is one of the most powerful applications of asymmetric encryption. It’s what gives us three vital security guarantees online: authentication (proof of who sent it), integrity (proof it wasn't tampered with), and non-repudiation (proof the sender can't deny sending it).
Here’s a simplified look at how it works:
- Create a Hash: First, the message is run through an algorithm to create a unique, fixed-length digital fingerprint called a hash.
- Encrypt the Hash: The sender then uses their own private key to encrypt this hash. This encrypted hash is the digital signature.
- Send the Data: The signature is then attached to the original message and sent off to the recipient.
- Verify the Signature: The recipient uses the sender's freely available public key to decrypt the signature, which reveals the original hash. They then run the message they received through the same hashing algorithm. If the two hashes match, the signature is valid.
This simple but brilliant process confirms the sender's identity (because only their private key could have created that signature) and proves the message is exactly as it was when it was sent.
