
How to Recover Lost or Stolen Cryptocurrency: Essential Tips
The first hour after you realize your crypto is gone is a blur, but it’s also the most critical window you have. What you do right now—in these first 60 minutes—can make or break any chance of getting your assets back. The game plan is simple: stop the bleeding, gather the evidence, and sound the alarm.
Your Crypto Is Gone: What to Do in the First 60 Minutes
That gut-wrenching moment you see an empty wallet is something no one should experience, but panic is the enemy here. You have to switch gears from victim to investigator, and you have to do it fast. Thieves work quickly, and they're already trying to muddy the waters by bouncing your assets through different wallets or pushing them into mixing services.
The very first move is damage control. If you think your computer or phone has been compromised, pull it off the internet immediately. Just unplug the ethernet cable or turn off the Wi-Fi. Don't shut the device down, though—that can wipe away crucial evidence from its active memory that a forensic expert might need.
If you know a specific hot wallet was hit, get any remaining funds out of there and into a secure, clean wallet. Ideally, this means a hardware wallet that’s never been connected to the infected device.
Identify and Document Everything
Once you’ve contained the breach, it’s time to become a detective. You need to gather every shred of evidence you can find. Don't guess; get the hard data.
Drill down into your transaction history and find the exact one that drained your funds. Here’s what you absolutely must collect:
- Malicious Transaction ID (TXID): This long string of numbers and letters is your smoking gun. It’s the unique identifier for the theft on the blockchain.
- Hacker’s Wallet Address: The destination address where your crypto was sent.
- Your Wallet Address: The address the funds were stolen from.
- Exact Timestamps: The precise date and time the transaction occurred.
- Amount and Type of Crypto: Be specific (e.g., 1.5 BTC, 10 ETH).
Screenshot everything. Your wallet interface, any sketchy emails or DMs you might have received, error messages—all of it. Save this evidence offline and back it up. This file is your case, and you'll need it for talking to exchanges and law enforcement.
Immediate Response Checklist
To help you stay focused under pressure, here’s a quick-glance table of what to do the moment you suspect a theft.
| Action Item | Why It's Critical | Information to Gather |
|---|---|---|
| Disconnect Device | Prevents further unauthorized access and theft from other wallets. | Note the date/time of disconnection. |
| Move Remaining Funds | Secures any assets the attacker hasn't already taken. | New secure wallet address. |
| Document the TXID | The primary piece of evidence for tracing funds on the blockchain. | The full Transaction ID (hash). |
| Identify Wallets | You need to know where funds went from and where they went to. | Your wallet address, the attacker's wallet address. |
| Record Timestamps | Helps exchanges and law enforcement build a timeline of the event. | Exact date and time of the transaction. |
| Contact Exchanges | Gives you a small window to freeze assets if they landed on a CEX. | All of the above, especially the TXID and destination address. |
Following this checklist methodically keeps you from missing a step when every second counts.
Making Critical Contact With Exchanges
Now, for a long shot that just might pay off. If you can trace the hacker's wallet address to a centralized exchange (CEX) like Coinbase, Binance, or Kraken, you need to act now. These platforms have security teams that can—and sometimes do—freeze accounts involved in theft.
Time is everything. You're in a race to get the exchange to flag the account before the thief cashes out or moves the crypto to a private, untraceable wallet. Once it leaves their system, the odds of recovery plummet.
Get in touch with the exchange’s support team through their official website or app. Give them all the evidence you’ve collected, leading with the transaction ID. Be professional and straight to the point. Tell them these are stolen funds and you need an immediate freeze on the receiving account while they investigate.
This flow chart really brings the initial response process to life, showing how you move from detection to action.
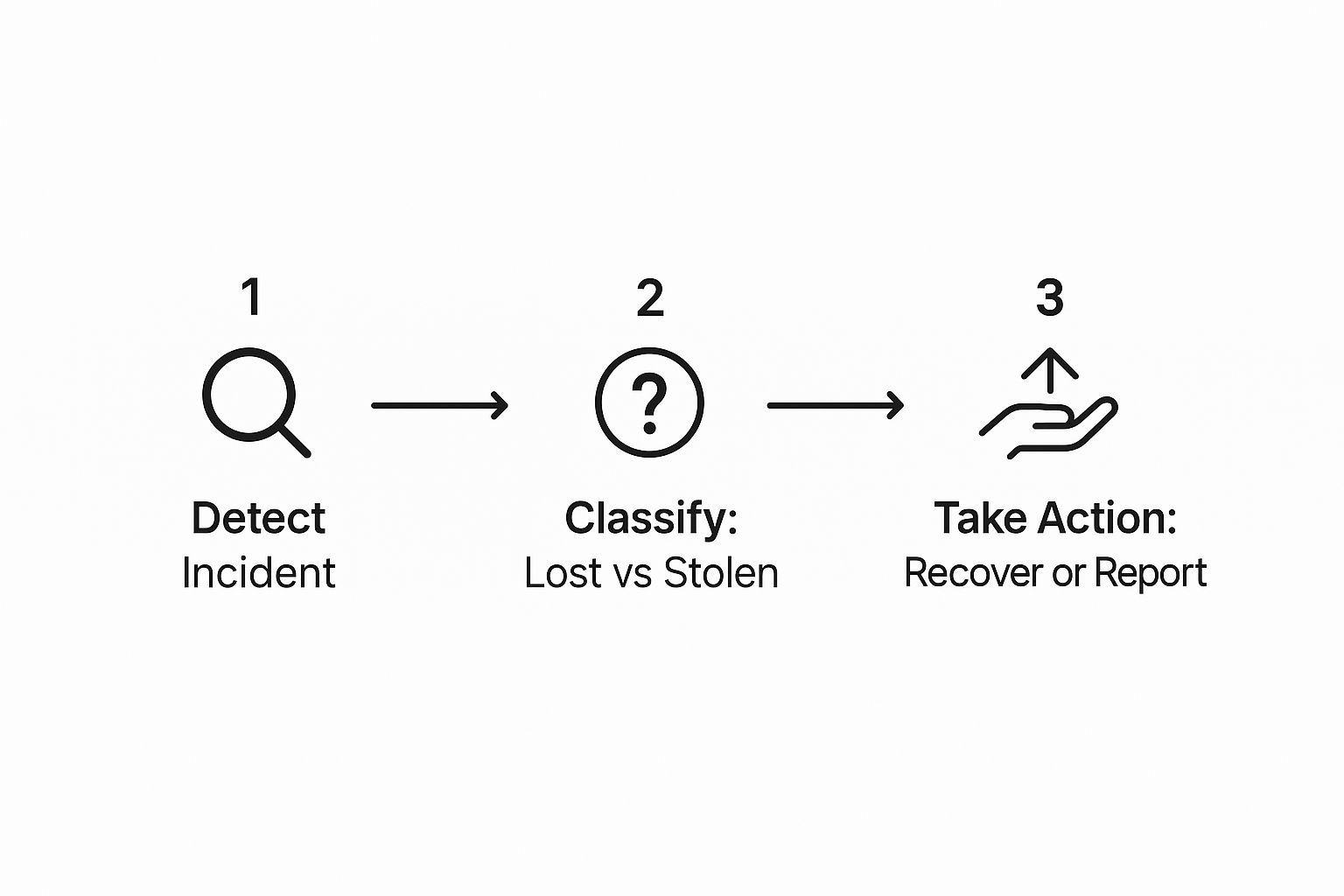
As the chart shows, how you react in these first moments dictates the entire path forward. It’s the difference between initiating a recovery effort versus just filing a loss report.
Don't get fooled by optimistic headlines, either. You might see stats claiming 70% recovery rates for crypto scams, but that’s incredibly misleading. In most major hacks where funds are professionally laundered, the real recovery rate is often less than 1%. The money gets tumbled through mixers and disappears. You can get a clearer picture from reports like the 2025 crypto crime mid-year update.
Following the Money: How to Trace Your Crypto on the Blockchain
Now that you've done the immediate damage control, it's time to switch gears from first aid to forensics. Think of yourself as a detective, because that's exactly what this part of the process requires. We need to follow the money.
The good news is that the blockchain is a public ledger. Every single transaction is recorded forever, creating a permanent digital trail. This trail is your best, and often only, source of evidence when trying to get your crypto back.
Your primary tool for this job is a blockchain explorer. It's basically a search engine for a specific blockchain. If we're talking about Ethereum or any ERC-20 token, you'll be using Etherscan. For Solana, it’s Solscan. Almost every major blockchain has one.
Kicking Off Your Investigation with a Blockchain Explorer
This part is less complicated than it sounds. You’ll take that malicious transaction ID (TXID) you found and paste it right into the explorer's search bar. That single action pulls up a page detailing everything about that specific transaction.
Here’s a real-world example of what you'll see on Etherscan when you look up a TXID.

This screen is packed with crucial info: the wallet that sent the funds, the wallet that received them, the exact amount, and a timestamp. This is ground zero for mapping out where your crypto went next.
From here, you can click on the receiving wallet address—the thief's address—and see its entire history. This is where the real detective work starts. You’re looking for patterns, for clues, for the attacker's next move.
- Jumping to Intermediary Wallets: Did the funds immediately hop to another, brand-new wallet? This is a classic move. Scammers use a chain of these "burner" wallets to try and muddy the waters.
- Splitting the Loot: Was the full amount split into smaller, random sums and scattered across multiple addresses? They do this to make the trail harder to follow.
- Cashing Out at an Exchange: The most important thing to look for is a transaction sent to a wallet address that belongs to a major exchange. Explorers often label these, and it's a huge lead.
Every transaction is a breadcrumb. Your job is to follow these crumbs until they lead to a centralized point—an exchange, a payment service—anywhere the thief might have had to link their real-world identity to the account.
This process of following the flow of funds is the core of on-chain security. To get a better sense of how professionals do this on a much larger scale, it’s worth reading up on what transaction monitoring is and why it’s so critical for catching bad actors.
The Make-or-Break Moment: Exchanges and Mixers
As you trace the path of your stolen funds, the best-case scenario is finding a transaction that leads directly to a well-known centralized exchange (CEX). Blockchain explorers are pretty good at tagging the deposit addresses for big players like Coinbase, Binance, or Kraken. If you see your crypto land in one of these tagged wallets, you've got them. Exchanges have KYC (Know Your Customer) data on their users, which is pure gold for law enforcement.
But the more sophisticated thieves know this. To cover their tracks, they’ll often use a crypto mixer or tumbler. These services are designed to deliberately obscure where crypto came from by mashing it together with funds from thousands of other users before spitting it back out.
Imagine a hacker puts 10 ETH into a mixer. The service pools it with thousands of other ETH deposits, shuffles it all up, and then sends 10 ETH out to a totally new, clean wallet the hacker controls. The on-chain link is effectively severed, making it nearly impossible for an amateur to trace it any further.
If you see your funds go into a notorious mixing service like Tornado Cash, the trail usually goes cold. At this point, your investigation is likely over, and it's time to hand your evidence to professional forensic firms. They have specialized tools that can sometimes de-anonymize mixer transactions.
Your goal is to document the journey up to this point as clearly as you can. Create a visual map of the transaction flow—from your wallet, through any intermediary wallets, and to its final destination at an exchange or mixer. This documentation becomes a powerful evidence package for the authorities or the recovery experts you bring in.
Engaging Professional Help and Legal Authorities

After you've done your own initial tracing, you're almost guaranteed to hit a wall. Whether the trail vanishes into a crypto mixer or gets tangled in a dizzying web of anonymous wallets, the path forward becomes incredibly murky. This is your cue to bring in the pros.
Trying to recover everything yourself is an uphill battle against highly skilled adversaries and a mess of international legal gray areas. Handing the reins to professionals and law enforcement puts the problem in the hands of people with the right tools, connections, and authority to navigate this world.
The scale of this problem is staggering. The year 2025 has been brutal, with thieves making off with over $3.1 billion in just the first six months. That figure blows past the $2.2 billion stolen in all of 2024. While there’s some good news—authorities and forensic firms have managed to freeze over $300 million in illicit funds this year—those wins almost always come from swift, expert-led action. These crypto scam recovery statistics really highlight the need to act fast.
Filing a Report with Law Enforcement
Your first official move should always be to report the theft to the police. In the United States, that means filing a detailed report with the FBI's Internet Crime Complaint Center (IC3). Most countries have a similar national agency dedicated to cybercrime.
When you file, treat it like you're building a case, not just telling a story. You need to provide them with actionable intelligence.
Here’s what your report must contain:
- A Clear Narrative: Write a step-by-step account of exactly what happened, how the theft was executed, and what you’ve done so far.
- The Complete Evidence: Hand over everything you've collected. This includes transaction IDs, wallet addresses (both yours and the thief's), exact timestamps, and copies of any messages or emails you had with the scammer.
- The Financial Damage: Clearly state the exact amount and type of crypto stolen and what it was worth in your local currency at the moment it was taken.
A well-documented police report is more than just a formality. It gives investigators the data they need to connect your incident to larger criminal rings. Often, your funds can be recovered as part of a much bigger seizure down the line.
This official report is also the key that unlocks other doors. Exchanges almost always require a case number before they'll cooperate with an investigation. It's also critical for any insurance claims or if you plan to write off the loss on your taxes.
Hiring Blockchain Forensic Specialists
While the police pursue the criminals, specialized private firms can dig into the technical side of the investigation. Companies like Chainalysis, CipherTrace, and Elliptic have incredibly powerful software that can often de-anonymize transactions, following the money far beyond what you can see on a public block explorer.
These services aren't cheap, but for high-value thefts, they can be a game-changer. Their job is to sift through mountains of blockchain data to find patterns, link anonymous wallets to real-world entities like exchanges, and arm law enforcement with the hard evidence they need to get subpoenas and warrants.
Be careful when choosing a firm. Legitimate investigators will never ask for your private keys and will never promise a guaranteed recovery. Anyone who guarantees they can get your funds back is lying. A reputable firm will typically charge a retainer or an hourly rate for their investigation, sometimes with an added success fee if they help recover your assets.
To get a better sense of what these experts can offer, it's worth understanding what private investigators do, as many now have teams specializing in digital asset recovery.
The Dangers of Recovery Scams
The unfortunate reality is that scammers love to prey on victims. The second you post about your loss on a public forum like Reddit or Twitter, your direct messages will be flooded with offers from "recovery agents."
These are almost universally scams. They play on your desperation, promising to get your money back for a "small" fee. They might even send you faked screenshots showing your crypto sitting in a wallet, claiming they just need a payment from you to "unlock" it. Don't fall for it.
Here’s how you can spot a recovery scam from a mile away:
- They contact you first. Real forensic experts don't slide into your DMs on Telegram. You find them; they don't find you.
- They guarantee results. No one can promise a 100% recovery. It's a complex process with no certain outcomes.
- They demand upfront fees. Scammers want their fee before they do anything. Legitimate firms bill you for their actual work.
- They ask for your private keys. This is the biggest red flag of all. NEVER share your seed phrase or private keys with anyone, ever. It’s like handing over the master key to your entire financial life.
Dealing with a crypto theft is a tough, emotional experience. By engaging the right authorities and being extremely cautious about who you hire for help, you can avoid being victimized a second time and give yourself the best shot at getting your assets back.
Understanding Why Most Stolen Crypto Is Never Recovered
Let’s start with a dose of reality, because it's the most important first step. The hard truth is that in most cases, stolen cryptocurrency is gone for good. Setting realistic expectations right now is one of the toughest but most crucial parts of this process.
Understanding why recovery is so difficult will not only arm you against false hope but also help you spot the predatory "recovery" scams that prey on victims in this exact situation.
The challenges are baked right into the technology. The very things that make crypto so appealing—decentralization and anonymity—are what make theft so permanent. Unlike a bank transfer that can often be reversed, blockchain transactions are immutable. Once a transaction is confirmed on the network, it’s set in stone. It cannot be undone, changed, or canceled by anyone.
Common Theft Scenarios and Their Recovery Odds
Not all crypto theft is the same. The "how" behind your assets being taken has a massive impact on the odds of ever seeing them again. A compromise of your private keys or seed phrase, for instance, is one of the most difficult situations to come back from.
If a scammer gets their hands on your seed phrase—maybe through a clever phishing attack or malware on your computer—they have total, unrestricted control. This is why fanatical security hygiene is non-negotiable. Knowing the best practices for secure seed phrase storage can be the one thing that stands between you and a total loss. Once an attacker drains your wallet, the funds are often laundered through a dizzying series of anonymous wallets in minutes, making any kind of trace a monumental task.
The type of scam also plays a huge role. Take rug pulls, where developers of a new project simply vanish with investors' funds. These are notoriously difficult to resolve. The infamous spike in rug pulls in 2021 led to a staggering $5.06 billion in losses, and almost none of it was ever clawed back. The perpetrators are anonymous ghosts from the start. You can see more data on how different crypto crimes impact recovery rates to get a clearer picture.
Here's the key takeaway: When funds are stolen from a self-custody wallet (like MetaMask or a hardware wallet), the responsibility—and the monumental challenge—of recovery falls almost entirely on you. A hack on a large, centralized exchange might offer a slim chance, but only because the exchange has legal obligations and may cooperate with law enforcement.
To put it plainly, the odds are stacked against you, but they vary depending on the crime.
Recovery Likelihood by Theft Type
This table breaks down the realistic recovery chances for some of the most common theft types. It’s not meant to discourage, but to provide a clear-eyed view of the situation.
| Theft Method | Typical Recovery Chance | Key Challenges |
|---|---|---|
| Phishing Scam | Very Low | Scammer has direct access to keys; funds are moved and mixed with incredible speed. |
| Rug Pull | Extremely Low | Perpetrators are anonymous by design, and funds are laundered almost instantly. |
| Exchange Hack | Low to Moderate | Recovery depends entirely on the exchange's cooperation, insurance, and law enforcement success. |
| Malware/Keylogger | Very Low | Similar to phishing; the attacker gains complete, undetected control of the wallet. |
As you can see, the direct-access methods that target your personal wallet are the most devastating and the hardest to recover from.
The Criminal's Toolbox for Covering Tracks
Skilled crypto thieves don’t just hit "send." The moment your assets are gone, they kick off a sophisticated laundering process to break the on-chain trail connecting them to the crime. Their only goal is to make the funds completely untraceable before they try to cash out into fiat currency.
They have a few go-to techniques to pull this off:
- Crypto Mixers (or Tumblers): These are services built to obscure the origin of funds. A thief sends stolen crypto to a mixer, which pools it with assets from thousands of other users. The service then spits out an equivalent amount of "clean" crypto to a new, unassociated wallet. The transaction link is effectively broken.
- Chain Hopping: This is a shell game played with different blockchains. They use decentralized exchanges to rapidly swap the stolen asset for another cryptocurrency, often multiple times in quick succession. For example, they might swap stolen ETH for Monero (XMR), then swap that XMR for BTC, creating a tangled mess of transactions across different ledgers.
- Privacy Coins: This is often the final step. Criminals love converting stolen funds into privacy-focused coins like Monero or Zcash. These currencies have privacy baked in, automatically hiding sender/receiver addresses and transaction amounts. This makes on-chain forensics nearly impossible.
Once your crypto goes into a mixer or gets converted to a privacy coin, the trail often goes cold for good. This is the main reason why knowing how to recover stolen crypto often begins with understanding the technical walls that prevent it. Acknowledging these realities is the first step toward focusing on what's actually actionable, not chasing false promises from fraudulent "recovery agents."
Fortifying Your Defenses with Proactive Security

Going through a crypto recovery is a nightmare. Once you’re on the other side, the focus has to shift to making sure it never, ever happens again. The best recovery strategy is prevention.
Building a fortress around your crypto isn't about being paranoid; it's about being smart. It means adopting a layered security approach that makes you a much harder target for criminals. This involves the right hardware, a healthy dose of skepticism, and disciplined daily habits.
Upgrading to Ironclad Wallet Security
Your first move, and the one with the biggest impact, is getting your crypto off exchanges and into a dedicated hardware wallet. I'm talking about devices from brands like Ledger and Trezor, which are built from the ground up to keep your private keys completely offline and away from internet-based threats.
Think of it this way: a hot wallet like MetaMask is convenient, like the cash you carry in your pocket. A hardware wallet is your own personal bank vault. Even if your computer is completely compromised with malware, the transaction has to be physically approved on the device itself, stopping a remote attacker cold. To really grasp why this is so critical, it's worth understanding https://blockbee.io/blog/post/what-is-cold-storage-wallet and its role as a security game-changer.
Simply buying a hardware wallet isn’t the whole story. You have to use it correctly. That means storing your seed phrase offline—etched in steel, not in a text file—and never, ever typing it into a computer or taking a photo of it.
For anyone with significant crypto holdings, a multi-signature (multi-sig) wallet is the next logical step. This setup requires multiple keys to sign off on a single transaction. Imagine a 2-of-3 multi-sig wallet: you hold one key, a trusted family member holds the second, and the third is locked away in a safe deposit box. A thief would need to compromise two of those separate, securely stored keys to move your funds. That’s a monumental challenge.
Mastering Your Human Firewall
All the best tech in the world can't protect you if an attacker tricks you into opening the door. The most common attack vector isn't some brute-force hack; it's you. Scammers have become masters of phishing and social engineering, designed to manipulate you into handing over your seed phrase or credentials.
Forget the poorly spelled emails from a Nigerian prince. Modern phishing attacks are incredibly sophisticated, with cloned websites that are pixel-perfect copies of the real thing. They use urgent "security alerts" and too-good-to-be-true airdrops to create a sense of panic or FOMO.
Here are a few hard-and-fast rules to live by:
- Never click links in emails or DMs. Always navigate to a crypto exchange or web wallet by typing the URL directly into your browser.
- Bookmark your go-to sites. Save bookmarks for every platform you use. This simple habit ensures you always land on the legitimate site, not a convincing fake.
- Question everything. If you get an email about a security breach, don't click the link. Open your browser, use your bookmark to go to the official site, and check for any notifications there.
This human element is a huge part of your security posture. For a deeper dive into this, you can find a lot of great information in guides covering network security essentials for protecting your digital assets.
Essential Daily Security Habits
Great security isn't about a one-time setup; it's about consistent, disciplined habits. Think of this as your personal checklist for turning your setup from an easy target into a hardened fortress.
- Unique, Complex Passwords: Use a password manager. It's non-negotiable. Let it generate and store a unique, long, and random password for every single account you have.
- Robust Two-Factor Authentication (2FA): Stop using SMS for 2FA. It's vulnerable to SIM-swapping. Switch to an authenticator app like Google Authenticator or, even better, a physical security key like a YubiKey.
- Keep Everything Updated: Your operating system, your browser, your wallet apps—update them immediately when prompted. These updates often contain critical patches for newly discovered security holes.
- Use a "Clean" Machine: If possible, dedicate one computer exclusively for crypto transactions. Don't use it for general web surfing, downloading files, or checking personal email. This dramatically reduces its exposure to malware.
By combining the physical security of hardware wallets, the structural defense of multi-sig, and the personal discipline of strong daily habits, you build a formidable defense that drastically lowers your risk of ever having to go through a recovery again.
Got Questions About Crypto Recovery? We've Got Answers
When you're dealing with a crypto incident, your head is probably swimming with questions. It's a stressful situation, and good information is hard to find. Let's tackle some of the most common concerns head-on.
Can I Get Back Crypto I Sent to the Wrong Address?
Honestly, the chances are slim. Blockchain transactions are final by design. Once a transaction is confirmed on the network, there’s no "undo" button. That's a core security feature, but it’s unforgiving when mistakes happen.
If you sent your crypto to a totally random address that no one controls, those funds are effectively lost in the digital ether. However, there's a sliver of hope if the address belongs to an actual person or a known entity.
For instance, if you accidentally sent funds to an address owned by a major exchange like Coinbase or Binance, you should immediately contact their support team. Provide the transaction ID and explain what happened. If they're willing to help, they might be able to return the funds, but don't count on it. They're not obligated to, and they'll almost certainly charge a fee for the trouble.
Are Crypto Recovery Services Legit?
You have to be incredibly careful here. The crypto recovery space is a minefield of scams. While there are legitimate blockchain forensic firms that can help trace stolen funds, they are vastly outnumbered by predators who target victims of theft.
Here’s how to spot a real professional from a scammer:
- They won't guarantee recovery. Anyone promising to get your crypto back is lying. A real expert knows it's a long shot and will only promise a thorough investigation.
- They will NEVER ask for your private keys or seed phrase. Giving this information away is like handing a thief the keys to your vault.
- They have a professional footprint. Look for a real company with a verifiable track record, a professional website, and a clear history—not just some anonymous account on Telegram or Twitter.
If someone randomly messages you on social media promising to recover your stolen crypto, it's a scam. 100% of the time. Real forensic experts are professionals you hire through proper channels; they don't cold-call victims.
What Does Professional Crypto Recovery Actually Cost?
Hiring a professional forensic firm isn't cheap, which is why it's usually reserved for cases involving significant amounts of money. Their pricing models can vary, but they generally fall into a few buckets.
- Upfront Retainer: You'll pay a fee just to get them started on your case. This secures their time and resources for the initial investigation.
- Hourly Billing: Just like a lawyer, they might charge you for every hour they spend digging through blockchain data and preparing reports for law enforcement.
- Success Fee: This is the most common model, where they take a cut of whatever they help recover. This commission can be anywhere from 10% to 40% of the recovered amount, and it's often on top of a retainer or hourly fees.
Before you agree to anything, make sure you get a detailed, written agreement that spells out every single potential cost. You need to weigh the very real cost of the investigation against the uncertain possibility of getting your funds back.
At BlockBee, we're firm believers that the best defense is a proactive one. Our non-custodial payment platform ensures you always have complete control over your funds, slashing the risk of hacks and third-party failures. Find out how our secure infrastructure can safeguard your business transactions at BlockBee's official website.
