
What Are Hardware Wallets and How Do They Work
Ever wondered what a physical vault for your digital money would look like? That's the best way to think about a hardware wallet. It’s a dedicated, physical device that keeps the private keys to your crypto assets completely offline, making them invisible and untouchable to online threats. This offline approach is known as cold storage, and it's a world away from the "hot" software wallets that live on your internet-connected computer or phone.
What's a Hardware Wallet All About?
At its heart, a hardware wallet is a small, specialized computer built for one single, critical job: to keep your private keys safe from the dangers of the internet. Your private keys are everything; they're the master key to your crypto safe. If someone gets them, they get your funds. While a software wallet stores this key on a device that's always online, a hardware wallet locks it away in a secure, isolated chip.
This physical separation is the secret sauce. When you need to send crypto, you connect the device to your computer. But here’s the magic: the private key never leaves the hardware wallet. The transaction details are sent to your device, you confirm everything on its little screen, and it signs the transaction internally. Only the secure, signed approval goes back to the computer—your keys remain safely offline the entire time.
The Shift to Secure Self-Custody
This method puts you in the driver's seat, giving you absolute control over your assets without needing to trust a bank or exchange. It’s no surprise that as people have become more aware of online security risks, these devices have become incredibly popular. This trend shows a clear move towards stronger security, with everyday users leading the charge in adopting hardware wallets.
This is what a typical hardware wallet looks like. Many resemble a USB drive and have a small screen for you to verify transactions before you approve them.
As you can see, they’re designed to be small and portable, making it easy to keep your digital wealth secure wherever you go.
To give you a clearer picture, let's quickly compare hardware wallets with their software counterparts.
Hardware Wallets At a Glance
| Feature | Hardware Wallet (Cold Storage) | Software Wallet (Hot Storage) |
|---|---|---|
| Key Storage | Completely offline on a dedicated device | Online on a computer or smartphone |
| Security Level | Highest; immune to online hacking/malware | Vulnerable to online attacks |
| Convenience | Requires physical device for transactions | Very convenient for quick, frequent trades |
| Best For | Long-term holding, large amounts of crypto | Daily spending, small balances, active trading |
This table sums it up well: if security is your top priority, especially for significant holdings, nothing beats a hardware wallet.
Why Should You Care?
The biggest win here is simple: protection from hackers. Since your keys never touch the internet, they can't be snatched by malware, phishing scams, or any other digital threat aimed at your computer. This makes hardware wallets a must-have for anyone serious about protecting their crypto for the long haul.
They are a cornerstone of the "be your own bank" philosophy that drives crypto. If you want to dive deeper into the different ways you can hold your own keys, you can learn more about non-custodial crypto wallets in our detailed guide.
A hardware wallet’s entire purpose is to make sure your private keys are never exposed to an online environment. Every crucial step, like signing a transaction, happens inside the device’s secure, offline bubble.
Ultimately, choosing a hardware wallet is about taking control. It's about minimizing how much you have to trust others and maximizing your own security in a world that's increasingly digital.
How Hardware Wallets Keep Your Crypto Safe
The real magic of a hardware wallet lies in one brilliantly simple security principle: keeping your private keys completely isolated.
Think of it like this: your private key is the master key to your crypto vault. A hardware wallet is a specialized safe designed only to hold that key. You can pass transaction requests into the safe to be signed, but the key itself never, ever comes out. It’s this total separation from your internet-connected computer that makes them the gold standard for security.
Every critical action, like signing a transaction, happens on a protected, purpose-built chip inside the wallet. This creates a secure offline bubble, a digital fortress that is completely cut off from your computer or phone. Even if your main machine is crawling with malware, those threats simply can't bridge the gap to reach your keys.
This graphic really drives home the security leap you make when moving funds from a vulnerable online wallet to the safety of a hardware wallet.
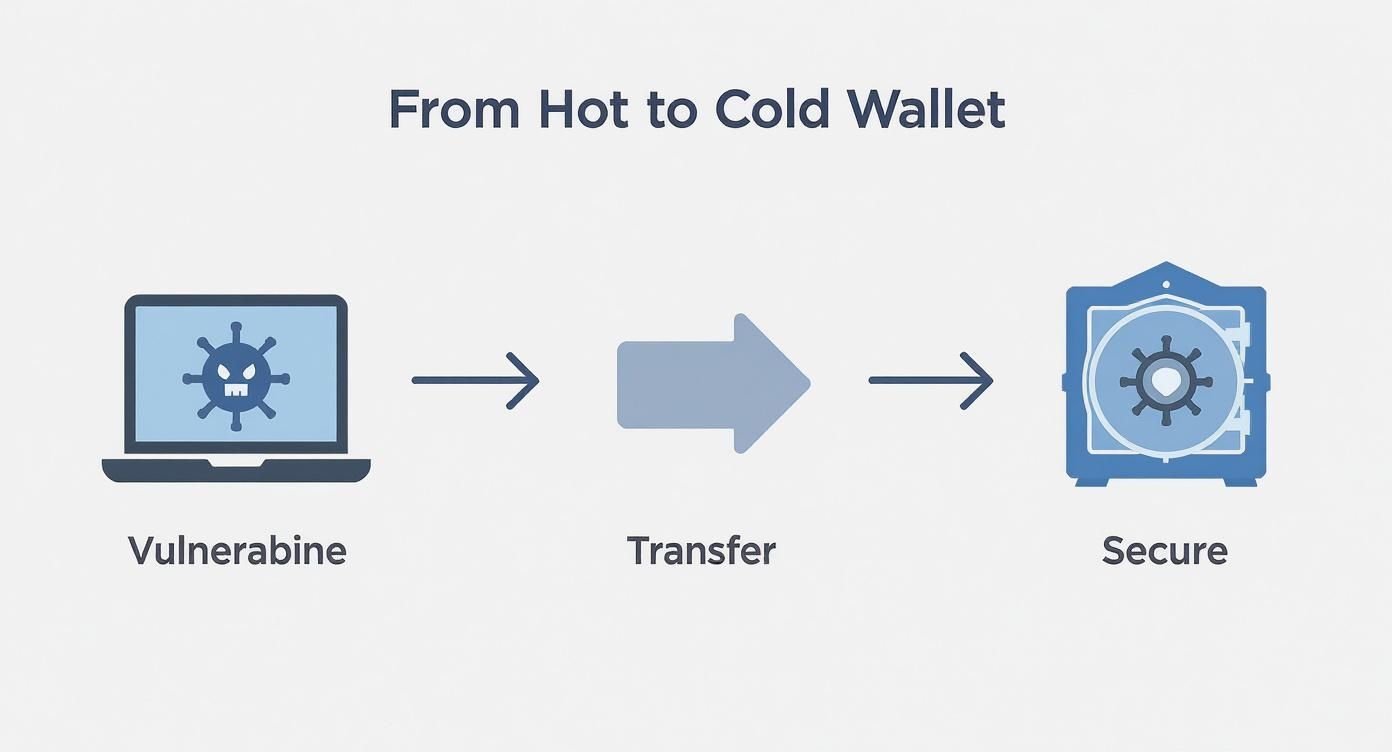
It’s a clear illustration of moving your assets out of a high-risk "hot" environment and locking them down in secure "cold" storage.
The Transaction Signing Process
So, what does this look like when you actually want to send some crypto? The entire process is designed to be very deliberate and hands-on, which is exactly what you want for security.
- Start the Transaction: First, you’ll open the wallet's companion app on your computer or phone and put together the transaction—entering the recipient's address and the amount.
- Verify on the Device: The app sends these details over to your plugged-in hardware wallet. Now for the most important step: you must check the details on the wallet's own little screen. This is your defense against screen-hijacking malware that might try to secretly change the address on you.
- Give Physical Approval: If the address and amount on the device's trusted display match what you intended, you physically press a button (or two) on the wallet itself to confirm.
- Sign Offline: Only after you give that physical green light does the wallet use the private key stored inside its secure chip to cryptographically sign the transaction.
- Broadcast to the Network: The newly signed transaction is then sent back to the app, which broadcasts it to the blockchain. At no point did your private key leave the hardware wallet.
This manual, multi-step process is a powerful form of multi-factor authentication (MFA), combining something you know (your PIN) with something you have (the physical device).
The Recovery Phrase: Your Ultimate Backup
But what if you lose the device, or it gets stolen or smashed? You might panic, but your crypto is perfectly safe. When you first set up any hardware wallet, it generates a recovery seed phrase—a unique list of 12 or 24 random words.
This recovery phrase is the ultimate master key to all your crypto. Write it down, store it somewhere safe (and offline!), and never, ever type it into a computer or take a picture of it.
If your device is gone, you just get a new one (it can even be from a different brand), enter your recovery phrase, and you’ll restore complete access to all your funds. The phrase regenerates your private keys on the new device, proving that the hardware is disposable, but your ownership is not.
This whole concept of offline security is the core of what we call cold storage. For a deeper dive, check out our guide on what is https://blockbee.io/blog/post/what-is-cold-storage-crypto and why it's so critical.
A Look at the Different Types of Hardware Wallets
Hardware wallets aren't a one-size-fits-all product. They come in all sorts of shapes and designs, and each one is built to meet different security needs and user preferences. Figuring out these differences is the first step in picking the right device to guard your digital assets. The world of hardware wallets is surprisingly diverse, with everything from devices that look like a simple USB stick to others as sleek as a credit card.
Think of it like choosing a lock. You wouldn't use the same flimsy padlock for your front door that you'd use for a high-security bank vault, right? It's the same idea here. Each hardware wallet strikes a different balance between convenience, portability, and raw security. Let's break down the main categories you'll run into.
USB-Style Wallets
The most common and recognizable hardware wallets are the ones that look a lot like a standard USB thumb drive. Brands like Ledger and Trezor have become household names in crypto, mostly because they nailed this familiar, user-friendly design. They’re small, easy to carry, and plug directly into a computer or smartphone with a USB cable.
This direct connection makes them incredibly practical for regular use. You just plug it in, punch in your PIN, and approve transactions using a companion app. Their little screens are a crucial feature, giving you a trusted place to verify transaction details before you physically press a button to confirm. That final, physical confirmation is a cornerstone of their security.
- Pros: Super portable, easy to get the hang of, and supported by a huge range of third-party software.
- Cons: The physical connection to an online device, while secure, does create a theoretical (though very small) attack vector.
- Best for: The everyday crypto user—from total beginners to active traders—who needs a secure and convenient way to manage their funds.
Here’s a great example of a modern USB-style wallet from Trezor. You can see its compact design and the clear screen used for verification.

This design is all about blending security with usability, using physical buttons to give you that final, tactile "yes" or "no" for any transaction shown on its screen.
Air-Gapped Wallets
For anyone who puts security above all else, air-gapped wallets are the holy grail. The term "air-gapped" means exactly what it sounds like: the device is engineered to have no direct physical or wireless connection to an online computer. It creates a complete electronic moat between your private keys and the internet.
So, how on earth do they work? Instead of using a USB cable, these wallets get creative to communicate transaction data:
- QR Codes: You'll start a transaction on a computer app, which then shows a QR code. You scan this code with the hardware wallet's built-in camera. The device signs the transaction internally and then displays a new QR code on its own screen. You then scan this new code with your computer's webcam to finally broadcast the signed transaction.
- SD Cards: The process is more manual here. The unsigned transaction data is saved to a microSD card. You then physically pop the card out of your computer and into the hardware wallet. After it signs the transaction, you move the card back to the computer to finish the process.
This whole song and dance completely sidesteps the risks that come with USB ports or Bluetooth connections.
By maintaining total electronic separation, air-gapped wallets offer a verifiable defense against even the most sophisticated remote hacks. The private keys never, ever touch a device that's connected to the internet.
Card-Shaped and Other Designs
A newer wave of hardware wallets is focused on making security incredibly simple and portable. These devices often look and feel just like a credit card. A perfect example is the Tangem wallet, which is as thin as a bank card and works by just tapping it against your NFC-enabled smartphone.
This kind of design innovation makes the idea of self-custody much less intimidating for a broader audience. There are no batteries to worry about charging or cables to lose.
- Pros: Extremely portable and discreet, often dead simple to set up and use.
- Cons: They rely on your smartphone's NFC, which not all phones have, and might lack some of the advanced features found on their USB-style cousins.
- Best for: Users who value convenience and portability for daily spending or those who want a simple, straightforward backup solution.
Ultimately, each type of hardware wallet comes with its own set of trade-offs. The right choice for you will really depend on your personal approach to security, how often you plan on making transactions, and your overall comfort level with the tech.
What to Look for When Choosing a Hardware Wallet

Picking a hardware wallet is a lot like choosing a safe. You wouldn't just grab the first one off the shelf; you'd check the lock, feel the thickness of the steel, and ask about the manufacturer's reputation. It's the same deal with securing your digital assets. It's easy to get fixated on price, but the features that deliver real peace of mind are what truly matter.
Not all hardware wallets are built the same, and what works for a day trader might be overkill for a long-term holder. Knowing what to look for will help you cut through the noise and find the right fit for your crypto.
Cryptocurrency and Token Support
First things first: Does this wallet even support the coins you own? This is the most basic, non-negotiable question. While pretty much every wallet out there supports heavyweights like Bitcoin and Ethereum, the support for altcoins, NFTs, and specific DeFi tokens can be all over the map.
Before you go any further, list out your assets and head straight to the manufacturer's website to check their supported crypto list. A wallet is just a fancy paperweight if it can't hold your coins.
The Security of the Chip
The heart of every hardware wallet is a special microchip called a secure element. Think of it as a tiny, digital Fort Knox. This is a tamper-resistant chip engineered to fend off both sophisticated digital hacks and physical attacks, making sure your private keys never see the light of day.
When you're comparing models, look for devices that use high-grade, certified secure elements. These chips have been battle-tested and offer a much higher level of security than a standard microcontroller. A top-tier secure element is the bedrock of the wallet's promise to keep your funds safe.
Your private keys are born inside this secure chip and never leave. It creates a completely offline, isolated vault, which is precisely how it stops malware on your computer from ever getting a peek at your keys.
Physical Durability and Design
Don't forget that a hardware wallet is a physical object. You’ll be handling it, carrying it, and storing it. The build quality really counts. What's it made of—cheap plastic or sturdy metal? Does it feel like it could survive a drop or a trip in a crowded backpack?
Some wallets are built like tanks, offering resistance to water, dust, or crushing force. While you hopefully won't be putting that to the test, a tough build gives you an extra layer of defense against life’s little accidents. The design also plays a huge role in how you use it, from the clarity of the screen to the clickiness of the buttons you'll use to sign off on every transaction.
Software and User Experience
A hardware wallet is only one-half of the puzzle. The other half is the software you use to manage everything. This app, whether on your desktop or phone, is your command center for your portfolio. A great app makes sending, receiving, and tracking your crypto feel effortless. A bad one makes it a chore.
Look for a clean interface and reliable performance. Some apps are stripped-down and simple, while others are packed with features like portfolio trackers and direct connections to decentralized exchanges. Be honest about your own tech-savviness here, because a clunky or confusing app can lead to frustration and costly mistakes.
- Easy Setup: How painless is the initial setup and backup process?
- Asset Management: Can you see your portfolio and transaction history at a glance?
- Third-Party Support: Does it play nice with other popular crypto apps you might use?
Company Reputation and Security Audits
Finally, the company behind the wallet is just as critical as the device itself. A brand worth its salt will have a long history of solid security, transparency, and regular firmware updates. You want to see companies that are open about their security measures and aren't afraid to have their hardware and software poked and prodded by independent auditors.
The market for these devices is growing fast, and it’s not just individuals anymore. Institutional and commercial use is expected to climb at a CAGR of around 31.05%, highlighting the need for trusted security partners. You can see this trend in the hardware wallet market research on imarcgroup.com. Ultimately, you’re picking a company you trust to protect your assets for years to come, which is especially vital when you consider the importance of proper seed phrase security.
How Businesses Use Hardware Wallets for Security
When you hear "hardware wallet," you probably picture an individual crypto investor keeping their assets safe. But the real heavy-lifting for these devices happens inside businesses, hedge funds, and other institutions. For them, a hardware wallet isn't just good security practice—it's a cornerstone of their entire risk management strategy.
Think about it: when a company is safeguarding millions of dollars in digital assets, a single point of failure is a non-starter. Hardware wallets give them what they need most: a way to take digital value and make it tangible and controllable, insulated from the constant barrage of online threats like hacks and phishing scams. It’s how they build a fortress around their corporate treasury.
Fortifying the Treasury with Multisig
One of the most powerful tools in the enterprise toolkit is multi-signature, or multisig. It’s a simple concept with massive security implications.
Imagine a high-security bank vault that requires two different managers to turn their keys at the same time to open the door. That's exactly how multisig works for crypto. It’s a digital two-key system.
A multisig setup demands that a transaction be approved by two or more separate hardware wallets before it's sent. A common arrangement for a business might be a "2-of-3" scheme:
- Key 1: Held by the CEO.
- Key 2: Held by the CFO.
- Key 3: Held by the Head of Security.
For a transaction to go through, any two of these three executives must physically sign off on it using their own device. This setup nearly eliminates the risk of a rogue employee draining the accounts or an attacker succeeding by compromising just one person's credentials. It’s the digital equivalent of checks and balances.
Beyond Storage: Advanced Controls and Compliance
For businesses, hardware wallet solutions are much more than just a place to store crypto. They’re comprehensive custody platforms built for organizational control and regulatory oversight.
For businesses, the conversation shifts from simple asset protection to robust operational security. Hardware wallets become the enforcement mechanism for internal financial controls in a decentralized environment.
This is a big reason why, even though individuals own more wallets, the commercial sector drives most of the market's revenue. Businesses need these advanced features to manage their holdings responsibly, a trend detailed in reports covering hardware wallet market statistics on coinlaw.io.
Key enterprise-grade features often include:
- User Role Management: Admins can set granular permissions. A junior accountant might get view-only access to check balances, while only a C-suite executive can actually sign and send a transaction.
- Auditable Transaction Logs: Every action is recorded. This creates an immutable audit trail that’s essential for financial reporting, satisfying regulators, or conducting an internal investigation.
- Policy Enforcement: Companies can hard-code their internal policies. This means setting spending limits, creating "whitelists" of approved addresses for payments, and defining other custom rules. Any transaction that breaks the rules is automatically blocked, catching human error or malicious activity before it happens.
These are the tools that allow a company to bring digital assets into their traditional treasury operations without sacrificing control. By building their processes on the security of hardware wallets, businesses can manage their crypto with the same discipline and rigor they apply to their bank accounts.
Got Questions? Let's Talk Hardware Wallets
Even with a solid grasp of how hardware wallets work, it's completely normal to have some "what if" questions buzzing around. These devices are a different way of thinking about security and ownership, so let's tackle some of the most common things people wonder about.
Getting these details ironed out is the final step to feeling genuinely confident with your crypto.
What Happens If I Lose My Hardware Wallet?
This is usually the first question on everyone's mind, and for a good reason. But here’s the reassuring answer: if your hardware wallet is lost or stolen, your crypto is perfectly safe. The device itself is just a sophisticated key; your actual funds are stored on the blockchain.
Think of it like losing the key to a safe deposit box at a bank. You can prove your identity, get a new key, and everything inside the vault is still untouched. The same idea applies here. As long as a thief doesn't know your PIN, the device is just a useless piece of plastic and metal to them.
To get back in control, you just need to:
- Grab a new hardware wallet. It can be the same brand or a different compatible one.
- During the initial setup, look for an option like "Restore from backup" or "Recover wallet."
- Carefully type in the 12 or 24-word recovery phrase you wrote down when you first set up the old device.
That recovery phrase is your true master key. It lets you rebuild your private keys on any compatible device, giving you instant access to your funds again. The hardware is disposable; your recovery phrase is everything.
Can a Hardware Wallet Get a Virus?
Nope. Hardware wallets are specifically engineered to be immune to viruses and malware. Your computer or phone runs a complex operating system with countless apps, creating a huge surface area for attacks. A hardware wallet is the complete opposite.
It’s a highly specialized, single-purpose device. Its internal chip, often a secure element, has only one job: to safeguard your private keys. It runs on simple, stripped-down firmware that doesn't allow any other software to be installed.
A hardware wallet acts like a secure, isolated vault for your keys. You can plug it into a computer that's crawling with malware, and the virus has no way to cross that electronic barrier to infect the wallet's secure chip.
This is the very essence of its security. All the important stuff—like signing transactions—happens inside this protected bubble, ensuring your keys are never exposed to the dangers of your internet-connected computer.
Are Hardware Wallets Hard to Use?
That's a common myth, but the reality is quite different. While the tech inside is complex, modern hardware wallets from companies like Ledger, Trezor, and Tangem are designed to be surprisingly user-friendly.
If you can handle a mobile banking app, you've got this. The whole process is designed to be smooth and intuitive, even for beginners.
Here’s what you can generally expect:
- Guided Setup: The device and its companion app will hold your hand through creating a PIN and backing up your recovery phrase.
- Simple Software: The app you'll use on your computer or phone gives you a clean, simple dashboard to see your assets and initiate transactions.
- Physical Confirmation: The most "technical" part is just looking at the transaction details on your wallet's little screen and physically pressing a button to approve it. It's a deliberate security check that quickly feels like second nature.
You definitely don't need to be a tech wizard to take full control of your crypto. These devices have made top-tier security accessible to everyone.
What If My Hardware Wallet Just Breaks?
Like any piece of electronics, a hardware wallet can fail. You might drop it, it could get wet, or it might just give up the ghost after years of service. But just like losing it, a broken wallet does not mean your crypto is lost forever.
As long as you have that recovery phrase stored safely, a dead device is just a minor inconvenience. You'd follow the exact same steps as if you'd lost it: get a new device, and use your 24-word phrase to restore your entire portfolio. This is why keeping that paper backup safe and sound is so incredibly important.
Ready to streamline your business's crypto operations with robust, non-custodial security? BlockBee offers a comprehensive B2B payment platform that puts you in full control. Accept payments, manage mass payouts, and integrate seamlessly with your existing e-commerce setup.
Explore how BlockBee can secure and simplify your crypto transactions today!
