
how do crypto wallets work: A Beginner's Guide to Digital Keys
Let's get one thing straight from the start: a crypto wallet doesn't actually hold your coins. It’s a common misunderstanding, but your assets always live on the blockchain itself.
Instead, think of your wallet as a highly secure keychain or password manager. It holds the cryptographic keys—the digital proof of ownership—that allow you to access and control your funds on the network. It's the essential tool that connects you to the blockchain.
What Your Wallet Actually Holds
To really get how a crypto wallet works, it's helpful to compare it to your bank account. Your wallet generates and protects two crucial pieces of data: a public key and a private key. These two keys are mathematically linked and form the backbone of your identity and security on the blockchain.
Your Keys to the Digital Kingdom
The entire security of cryptocurrency rests on the relationship between these two keys. They use a clever type of cryptography called asymmetric encryption, which makes sure that only you can access and spend your funds. If you're curious about the technical nuts and bolts, we cover the topic in our guide on symmetric and asymmetric encryption.
Here’s a simple breakdown of what each key does:
Public Key: This is generated from your private key and is used to create a public address. It’s perfectly safe to share this address with anyone who needs to send you crypto. Think of it like your bank account number or even your email address—it's for receiving things.
Private Key: This is the big one. It's a secret, complex code that acts as the ultimate master key to your funds. Your private key digitally "signs" (or authorizes) every transaction you send, proving to the network that you’re the rightful owner. You should never, ever share your private key with anyone.
The easiest way to remember the difference is this: Your public address is for receiving funds, while your private key is for sending them. If you lose your private key, you lose your crypto. It's that simple, and there's no "forgot password" button.
How Your Wallet Creates an Address
Your wallet takes that long, messy public key and uses a process called hashing to turn it into a shorter, more manageable public address. This is the string of letters and numbers you copy and share to get paid. For instance, a Bitcoin address might start with a 1 or a 3, while an Ethereum address almost always begins with 0x.
This key-and-address system is the foundation for every type of wallet, from custodial ones where a third party holds the keys for you, to non-custodial wallets where you are in complete control. As crypto becomes more mainstream, with transaction volumes climbing in places like the United States and India, understanding this core concept is more critical than ever.
To make it even clearer, here's a quick summary of the essential parts of a crypto wallet.
Key Components of a Crypto Wallet
| Component | Analogy | Primary Function |
|---|---|---|
| Private Key | Your ATM PIN or master password | Authorizes (signs) outgoing transactions. Proof of ownership. |
| Public Key | Your bank account number | Generates your public address. Used to verify your signature. |
| Public Address | Your email address or home address | A shareable identifier for receiving cryptocurrency. |
Ultimately, these three components work together seamlessly to give you a secure and reliable way to interact with the blockchain.
Anatomy of a Crypto Transaction
So you've got a handle on public and private keys. Now for the fun part: let's see how they actually work when you send crypto. We'll follow a transaction from the moment you hit "send" in your wallet all the way until it's set in stone on the blockchain. This journey really gets to the heart of how wallets move value securely without anyone in the middle.
Let's say you want to send some Bitcoin to a friend. You’ll open your wallet, paste their public address, and punch in the amount. When you confirm, your wallet software takes all that information—the amount, the destination address, and your own address—and packages it up.
This is where your private key does its most important job. Your wallet uses that key to generate a digital signature for this specific transaction. Think of it as your unique, unforgeable stamp of approval. It cryptographically proves that you authorized the payment, all without ever showing your private key to anyone.
This diagram breaks down the core relationship between your keys and your wallet.
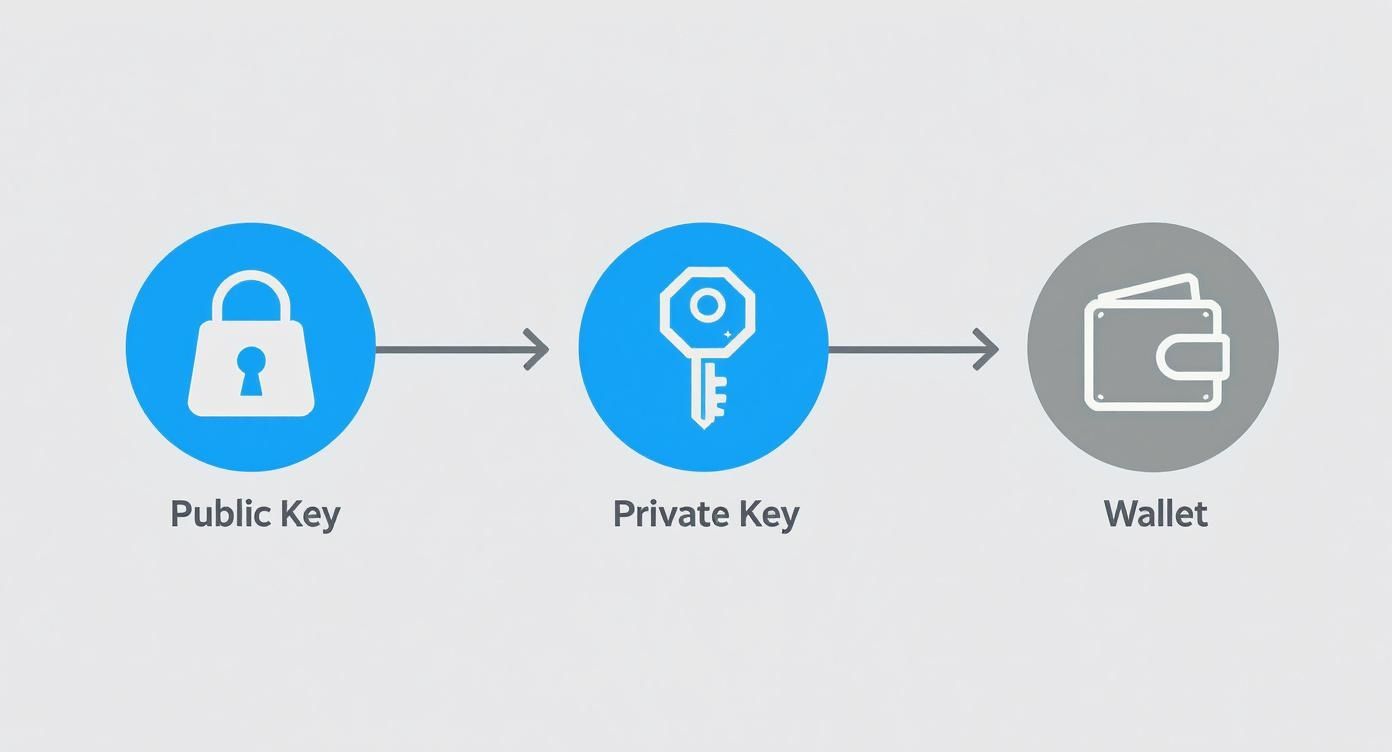
As you can see, your public key is meant to be shared, but your private key is what your wallet uses to unlock your funds and sign off on any action. Keeping it safe is everything.
From Your Wallet to the Blockchain
Once signed, your wallet broadcasts the transaction out to the entire crypto network. It’s like announcing the transaction in a massive, public square where everyone is listening. From there, it lands in a digital waiting room called the mempool (memory pool), which is just a big, unorganized list of all the transactions waiting to be processed.
This is where miners (on Proof-of-Work chains like Bitcoin) or validators (on Proof-of-Stake chains) step in. They grab your transaction from the mempool and run a few critical checks:
- Verify the Signature: They use your public key to make sure your digital signature is legit and matches the transaction details.
- Check for Sufficient Funds: The network scans the blockchain to confirm your public address actually holds enough crypto to cover the payment.
- Prevent Double-Spending: They ensure you haven’t tried to send the exact same coins to someone else in a different transaction.
A transaction is only considered valid if it passes all these cryptographic checks. This decentralized verification is precisely what removes the need for a bank, making the whole system secure and "trustless."
After your transaction passes inspection, it gets bundled with a bunch of other verified transactions into a new "block." This block is then permanently chained to the one before it, officially adding it to the blockchain's immutable record. Once it’s on the chain, the deal is done—the funds are now reflected in your friend's wallet.
Custodial vs. Non-Custodial: Who Really Controls Your Keys?
When you’re picking a crypto wallet, the most important decision you'll make boils down to one question: who holds the private keys? This choice fundamentally defines your control over your digital assets. The two paths—custodial and non-custodial—offer completely different answers.
Think of a custodial wallet like a bank account. The bank, in this case a crypto exchange or a third-party service, holds the keys for you. It’s convenient, sure. If you forget your password, they can help you get back in. The catch is you're placing your complete trust in them to keep your assets safe and give you access whenever you ask.
A non-custodial wallet, on the other hand, is like having a physical safe in your own home. You, and only you, hold the keys. This gives you absolute control and sovereignty over your funds. It’s the embodiment of the famous crypto mantra: "not your keys, not your coins."
The Custodial Wallet Tradeoff: Convenience for Control
Custodial wallets, which are what you typically get on major crypto exchanges like Coinbase or Binance, are incredibly popular with newcomers. Why? Because the setup feels familiar—just an email and password, and you're ready to go. This simplicity has been the front door for millions of people stepping into the world of crypto.
But this ease of use comes at a price. You're handing over immense trust to the service provider. If that exchange gets hacked, goes bankrupt, or freezes your account, your funds could be lost or inaccessible. You're essentially trading direct ownership for a user-friendly experience.
Taking the Reins with Non-Custodial Wallets
Non-custodial wallets put you firmly in the driver's seat. You are solely responsible for protecting your private keys and your all-important recovery phrase. This is the very foundation of true digital ownership and a massive part of what draws people to crypto in the first place. You can dive deeper into the benefits and responsibilities in our complete guide on non-custodial crypto wallets.
The fundamental difference is responsibility. With a custodial wallet, you trust a third party. With a non-custodial wallet, you trust yourself.
The demand for self-sovereignty is skyrocketing. The global crypto wallet market is projected to explode from USD 12.59 billion in 2024 to well over USD 100 billion by 2033. A huge part of this growth is fueled by users who want more control, with non-custodial wallets now handling over 70% of digital asset transactions in certain areas. You can find more details about this market growth on nadcab.com. Opting for a non-custodial solution puts you at the forefront of this powerful movement.
Custodial vs Non-Custodial Wallets Key Differences
To make the choice clearer, let's break down the core differences side-by-side. What you value most—be it convenience, security, or total control—will point you to the right solution.
| Feature | Custodial Wallet (e.g., Exchange) | Non-Custodial Wallet (e.g., MetaMask, Ledger) |
|---|---|---|
| Private Key Control | Third party holds the keys | You hold the keys |
| Security Responsibility | You trust the provider's security | You are 100% responsible |
| Account Recovery | Simple password reset | Only possible with your seed phrase |
| Ease of Use | Very beginner-friendly | Steeper learning curve |
| Access to Funds | Can be frozen or limited by provider | Unrestricted, censorship-resistant access |
| Best For | Beginners, traders, convenience seekers | Long-term holders, DeFi users, sovereignty advocates |
Ultimately, there's no single "best" answer—only what's best for your specific needs. For a business handling customer funds or a beginner making their first trade, a custodial service might make sense. For an individual who wants to truly own their digital assets, non-custodial is the only way to go.
Hot Wallets vs. Cold Wallets: Balancing Access and Security
Beyond deciding who holds your keys, you need to think about where those keys are stored. This is the fundamental difference between hot wallets and cold wallets, and it’s a critical piece of the security puzzle.
The distinction couldn't be simpler: a hot wallet is connected to the internet, and a cold wallet is not.
Think of your hot wallet as your checking account. It’s perfect for everyday spending and quick transactions, holding just the funds you need easy access to. Your cold wallet, on the other hand, is like a bank vault. It's the highly secure, offline fortress where you store the bulk of your assets for the long haul.

This one difference—internet connectivity—has massive implications for how your wallet works and how vulnerable it is to attack.
Hot Wallets: Your Everyday Spending Account
Hot wallets are software-based and live online. This makes them incredibly convenient for day-to-day use but also leaves them more exposed. Because they're always connected, they're a prime target for hackers and malware designed to hunt for and steal private keys.
You'll find hot wallets in a few common forms:
- Mobile Wallets: Smartphone apps for managing your crypto on the go.
- Desktop Wallets: Software programs you install directly onto your computer.
- Web Wallets: Browser extensions or interfaces you access online, often provided by exchanges.
The trade-off for convenience is that your private keys are stored on a device that’s constantly online, creating a persistent attack surface. While wallet developers build in robust security features, the risk from online threats can never be completely erased.
Cold Wallets: The Fortress for Your Assets
Cold wallets, also known as cold storage, take your private keys completely offline. This “air-gapped” approach erects a powerful wall against remote digital attacks like hacking, phishing, and malware. Your keys only interact with an online device for the brief moment it takes to authorize a transaction.
The most common types of cold storage are:
- Hardware Wallets: Physical devices, often looking like a USB stick, that sign transactions internally without ever exposing the key.
- Paper Wallets: A simple piece of paper with your public and private keys printed on it.
The real security magic of a cold wallet is that your private key never touches an internet-connected computer. This physical isolation is the gold standard for personal crypto security.
For any serious investor or business handling significant funds, a hybrid approach usually makes the most sense. Keep a small, manageable amount in a hot wallet for quick payments and daily use, while securing the vast majority of your assets in a cold wallet. This gives you the best of both worlds: everyday convenience paired with fortress-like security.
Essential Security Practices for Every Wallet User

Getting a handle on how crypto wallets work is only half the battle. The real work begins when you take responsibility for securing them. In the world of crypto, you're not just a user—you're your own bank, which means you're also your own head of security.
That shift in mindset is more important than ever. By 2024, the global crypto community grew to over 560 million people, and a huge part of that growth comes from mobile wallet adoption. While that’s exciting, it also makes robust security habits absolutely non-negotiable. You can dig into the numbers yourself by checking out the latest crypto adoption statistics on Statista.
Protect Your Seed Phrase Like a Vault
Your seed phrase (often called a recovery phrase) is, without a doubt, the most critical piece of information you own for a non-custodial wallet. Think of it as the master key to your entire financial life in crypto. It’s what lets you restore your wallet and access all your funds on a new device.
If you lose it, your crypto is gone forever. If a thief gets it, your crypto is as good as theirs.
Your private key signs transactions, but your seed phrase lets someone recreate your private key from scratch. Never, ever store it digitally. That means no screenshots, no cloud backups, and no password managers.
Write it down on paper—or better yet, engrave it on metal—and hide it in a secure, offline location. In fact, use multiple secure locations. This one habit is the foundation of self-custody. For a deeper dive, check out our guide on proper seed phrase security.
Actionable Security Habits to Adopt Today
Securing your seed phrase is step one. To truly protect your assets, you need to build a few smart habits into your routine.
Use a Hardware Wallet: If you're holding any amount of crypto you can't afford to lose, move it to a hardware wallet. These devices keep your private keys completely offline, making them untouchable by online hacks and malware.
Beware of Phishing: Scammers are clever. They build convincing fake websites and send official-looking emails designed to trick you into giving up your seed phrase or private keys. Always be skeptical, double-check every URL, and never click on unsolicited links asking for your info.
Enable Two-Factor Authentication (2FA): For any accounts on exchanges or other custodial platforms, turn on 2FA immediately. And don't just use SMS—use a dedicated authenticator app like Google Authenticator. It adds a powerful layer of defense against someone trying to break into your account.
Putting Crypto Wallets to Work for Your Business
So far, we've talked about crypto wallets from a personal perspective. But for entrepreneurs and developers, they're much more than just a place to hold digital assets—they're powerful tools for business.
Integrating wallet technology can open up entirely new ways to get paid, manage company funds, and even build services that run on the blockchain. We're talking about more than just slapping a wallet address on your website. Modern wallet APIs let you build sophisticated payment flows that feel slick for customers and are a breeze for your team to manage. You can create anything from a simple "Pay with Crypto" button to complex financial products.
The real challenge for any business is bridging the gap between the technical nuts and bolts of crypto and creating a smooth, intuitive user experience. You'll be solving problems at a scale that most individual users never encounter.
Designing Your Wallet Integration Strategy
When you decide to bring crypto payments into your business, your first big choice is about custody. Are you going to manage your own keys and infrastructure (going non-custodial), or will you let a third-party payment processor handle the heavy lifting? Each route has major implications for your security, costs, and overall control.
A self-managed, non-custodial setup gives you total control over your funds, but it demands serious technical know-how to keep everything secure. On the flip side, using a payment gateway like BlockBee makes life much easier by offloading the technical burden, letting you focus on what you do best—running your business.
Any business in this space has to get familiar with financial regulations. When you're using crypto wallets, that absolutely includes tax rules. Properly accounting for every transaction is non-negotiable, and resources on understanding crypto tax implications are a great place to start.
Key Considerations for Business Implementation
Getting your crypto wallet integration right means thinking carefully about a few key areas. Nailing these is crucial if you want to build a secure, user-friendly product that people will actually trust and use.
User Onboarding: Think about your customer. How will you guide someone new to crypto through their first payment? The flow has to be dead simple, with minimal jargon and clear instructions. A confusing checkout is a lost sale, guaranteed.
Transaction Fee Management: Network fees, or "gas," can be unpredictable and swing wildly. You need a strategy for this. Will you eat the cost, pass it to the customer, or maybe use a Layer 2 network to bring fees down?
Payouts and Reconciliation: How are you going to handle paying suppliers or employees in crypto? If you're running an e-commerce store, matching crypto payments to sales orders needs to be just as seamless as it is with credit cards. This is where features like Mass Payouts and solid reporting become essential for keeping operations running smoothly.
By tackling these challenges head-on, you can move past simply accepting crypto and start building genuinely useful products that take advantage of what blockchain technology truly offers.
Common Questions About Crypto Wallets
To wrap things up, let's tackle some of the most common questions that pop up when people are getting the hang of crypto wallets. These are the practical, real-world concerns that are crucial to understand.
What Happens If I Lose My Wallet?
It’s a scary thought, but what happens next depends entirely on the kind of wallet you’re using.
For a non-custodial wallet, losing the physical device or deleting the app isn't the end of the world if you have your seed phrase. You can simply grab a new wallet (or re-install the app) and use that phrase to restore full access to all your crypto. This is exactly why that little list of words is the most important thing to protect.
With a custodial wallet, like an account on a major exchange, the process is much more familiar. You'll go through a standard account recovery flow, similar to resetting a password for your online banking.
Can One Wallet Hold Different Kinds of Crypto?
Absolutely. Most modern wallets are multi-currency, which means you can manage Bitcoin, Ethereum, Solana, and many others all from one place.
But there's a catch: you have to be sure your wallet specifically supports the coin you want to receive. Sending crypto to an address on the wrong network is one of the easiest—and most permanent—ways to lose it. Always double-check.
It's a common misconception that wallets "hold" coins. They don't. A wallet holds the keys that give you control over your assets, which live on their respective blockchains. A multi-currency wallet is really just a great key manager for different networks.
Why Are Transaction Fees So Unpredictable?
Those fluctuating transaction fees (often called "gas fees" in the Ethereum world) aren't set by your wallet. They're dictated by simple supply and demand on the blockchain itself.
When the network gets busy, everyone is competing for limited space in the next block. To get their transaction included quickly, people offer higher fees. Your wallet just looks at the current state of the network and suggests a fee that’s likely to get your transaction processed without a long wait.
Ready to make crypto payments simple for your business? BlockBee provides a secure, non-custodial gateway that takes the headache out of accepting crypto. Enjoy low fees, instant payouts, and a straightforward integration, so you can get back to what you do best. Learn how BlockBee can help your business today.
